Back
Gigaversity
Gigaversity.in • 8m
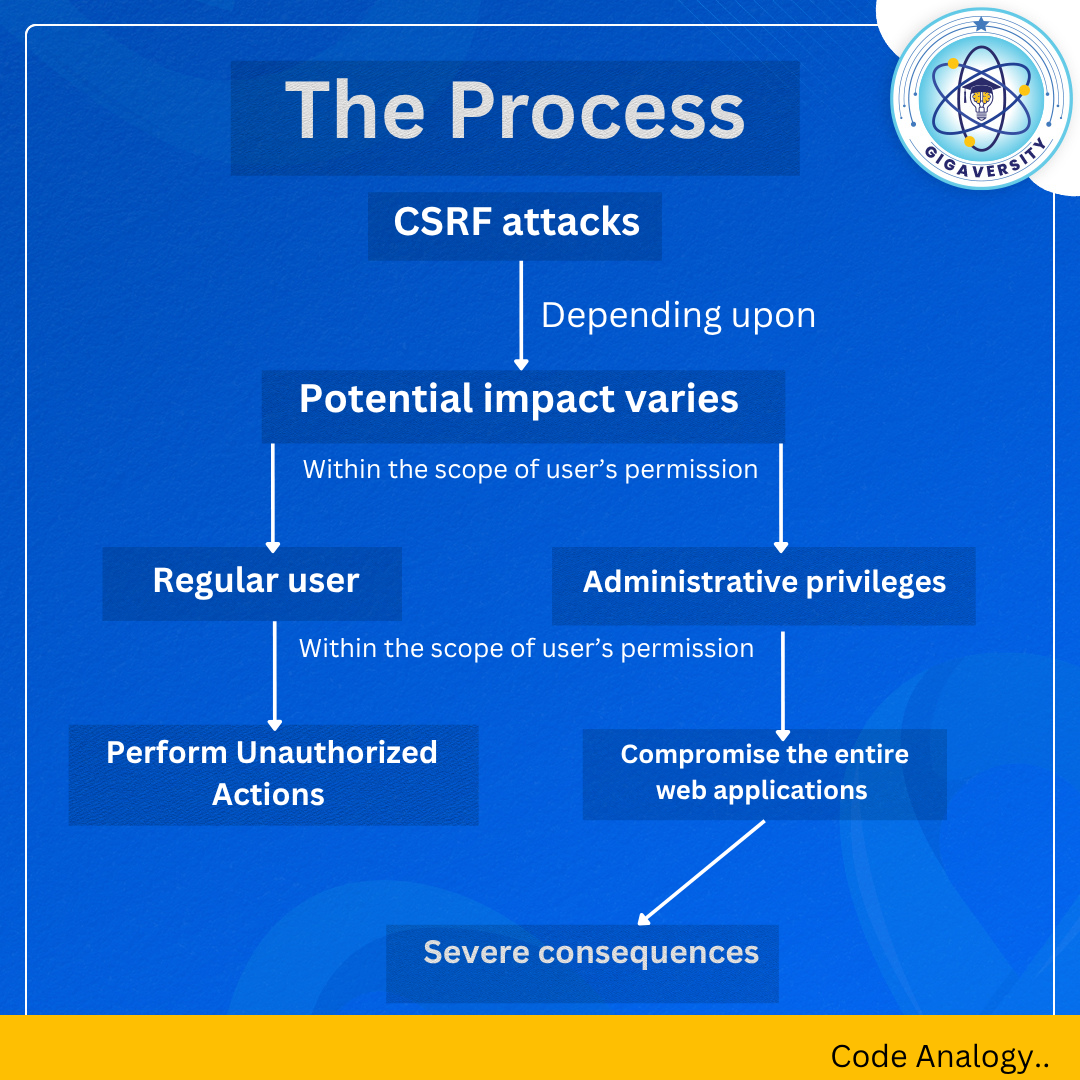
Web apps are getting smarter — so are the attacks targeting them. Two of the most common threats that silently compromise user trust? CSRF and XSS. They might sound similar, but their impact and execution are very different. From hijacking user sessions to injecting malicious scripts, these attacks exploit vulnerabilities that developers must understand and guard against. Swipe through to get a clear picture of how these attacks work and how you can stay one step ahead. Follow Gigaversity on linkedin for complete Code Analogy series.

More like this
Recommendations from Medial
Vansh Khandelwal
Full Stack Web Devel... • 1y
Security testing ensures that applications are free from vulnerabilities like SQL Injection, XSS, CSRF, and IDOR. SQL Injection occurs when unsanitized inputs allow attackers to manipulate database queries. This can be mitigated by using parameterize
See MoreSheikh Ayan
Founder of VistaSec:... • 11m
10 Advanced Red Teaming Tactics for Unbeatable Cyber Resilience 🚨💻 Red teaming is not just about hacking—it's about thinking like real-world adversaries to uncover hidden weaknesses before they do. Here are 10 advanced tactics used by elite threat
See MoreSheikh Ayan
Founder of VistaSec:... • 10m
Bypassing EDR with Custom Shellcode Loaders – A Red Teamer's Approach Modern EDRs use user-mode hooks, behavioral analysis, and memory scanning to flag malicious activity. To bypass them, you need precision-crafted tooling. This deep-dive explores
See MoreSheikh Ayan
Founder of VistaSec:... • 11m
🔒 How to Secure Your System & Servers Like a Pro! 🚀 Follow these advanced tips to safeguard your systems and servers from potential attacks: ✅ Enable Multi-Factor Authentication (MFA) – Add an extra layer of security beyond passwords. 🛡 Implemen
See MoreSheikh Ayan
Founder of VistaSec:... • 12m
🚨 Top IoT Vulnerabilities You Need to Know! 🚨 🔹 Weak Passwords & Default Credentials – Many IoT devices ship with default passwords that are easy to guess. 🔹 Unpatched Firmware – Outdated software can have security flaws that hackers exploit. 🔹
See MoreDownload the medial app to read full posts, comements and news.









/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)





















