Back
Sheikh Ayan
Founder of VistaSec:... • 12m
🚨 Top IoT Vulnerabilities You Need to Know! 🚨 🔹 Weak Passwords & Default Credentials – Many IoT devices ship with default passwords that are easy to guess. 🔹 Unpatched Firmware – Outdated software can have security flaws that hackers exploit. 🔹 Insecure Network Connections – Lack of encryption makes data transmissions vulnerable to interception. 🔹 Lack of Access Control – Unauthorized users can easily take control of poorly secured devices. 🔹 Insufficient Data Protection – Sensitive information is often stored or transmitted without proper encryption. 🔹 Botnet Attacks – Compromised IoT devices can be recruited into massive botnets for cyberattacks. 🔹 Lack of Security Updates – Many IoT manufacturers fail to provide regular patches or updates. 🔒 How to Stay Secure? ✅ Change default passwords immediately ✅ Regularly update firmware and software ✅ Use strong encryption protocols ✅ Restrict device access and use firewalls ✅ Monitor network traffic for unusual activity
Replies (4)
More like this
Recommendations from Medial
Pulakit Bararia
Founder Snippetz Lab... • 7m
I have been building apps with the help of AI agents but there’s always been one major flaw: No real security. No tamper protection. No local encryption. No defense against rooted or compromised devices. So, we built Novo — a fully offline, ultra-s
See More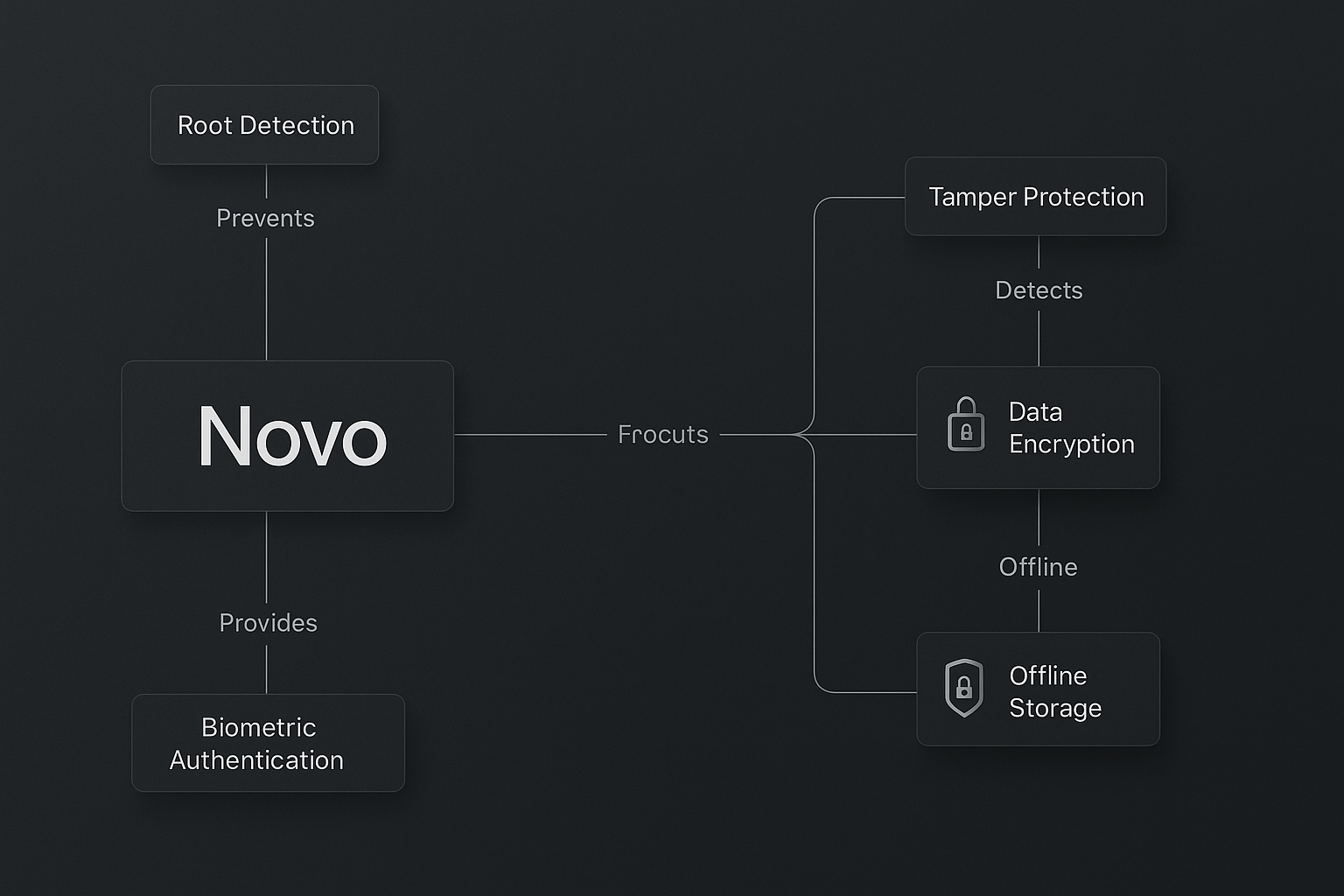
Sheikh Ayan
Founder of VistaSec:... • 1y
IoT Hacking Hardware Devices – Understanding Security Risks IoT devices are everywhere—from smart homes to industrial automation. But how secure are they? IoT hacking hardware plays a crucial role in security research, penetration testing, and ethic
See MoreSaswata Kumar Dash
Buidling FedUp| AI R... • 8m
🚨 This week in AI + Tech is next level 👇 ✅ 16 BILLION PASSWORDS LEAKED (Apple, Google, Meta & more) ✅ Meta drops $15B on Superintelligence ✅ Witcher 4 returns in Unreal Engine 5 ✅ Roblox breaks all-time record — 16.4M players online! 📺 Watch ALL
See MorePuneet singla
Founder & Managing D... • 11m
🚨 AI-Powered Wearable Safety System for Women 🚨 Crimes like rape and murder happen because help doesn’t reach on time. What if a smart wearable gadget could change this? I am working on an AI-based Wearable Safety System that can be triggered by
See MoreDownload the medial app to read full posts, comements and news.

















/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)




















