Back
Vansh Khandelwal
Full Stack Web Devel... • 1y
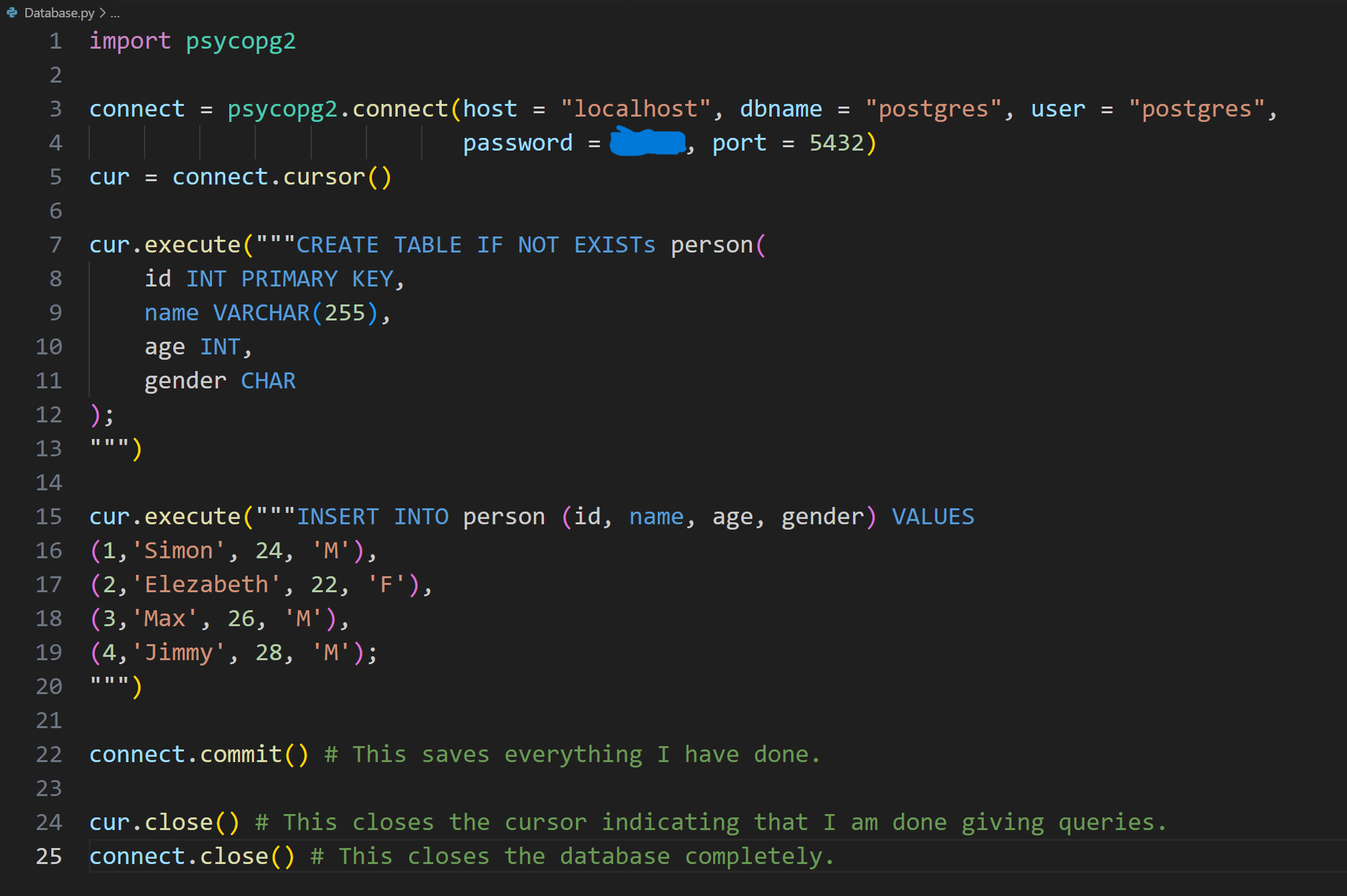
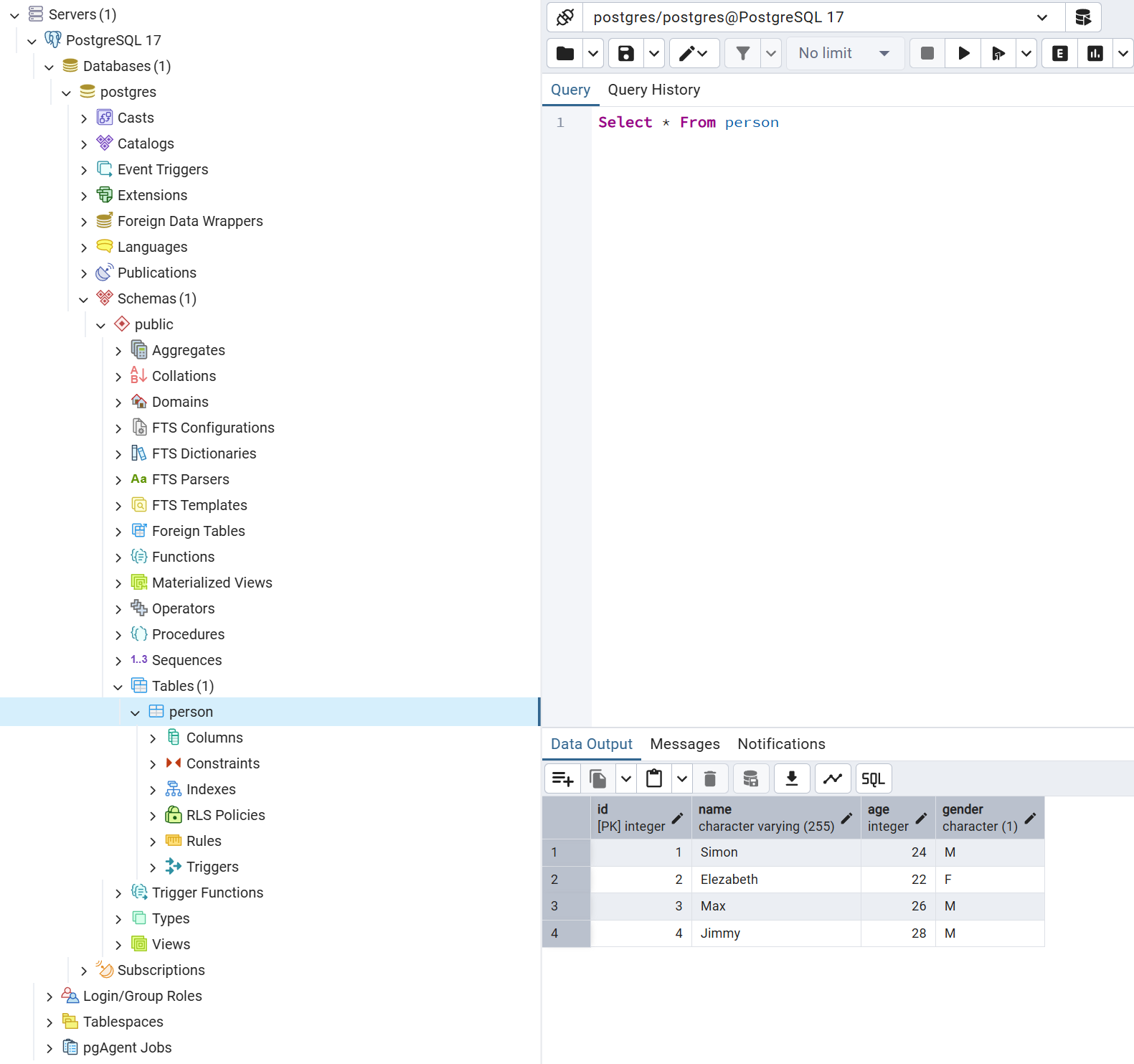
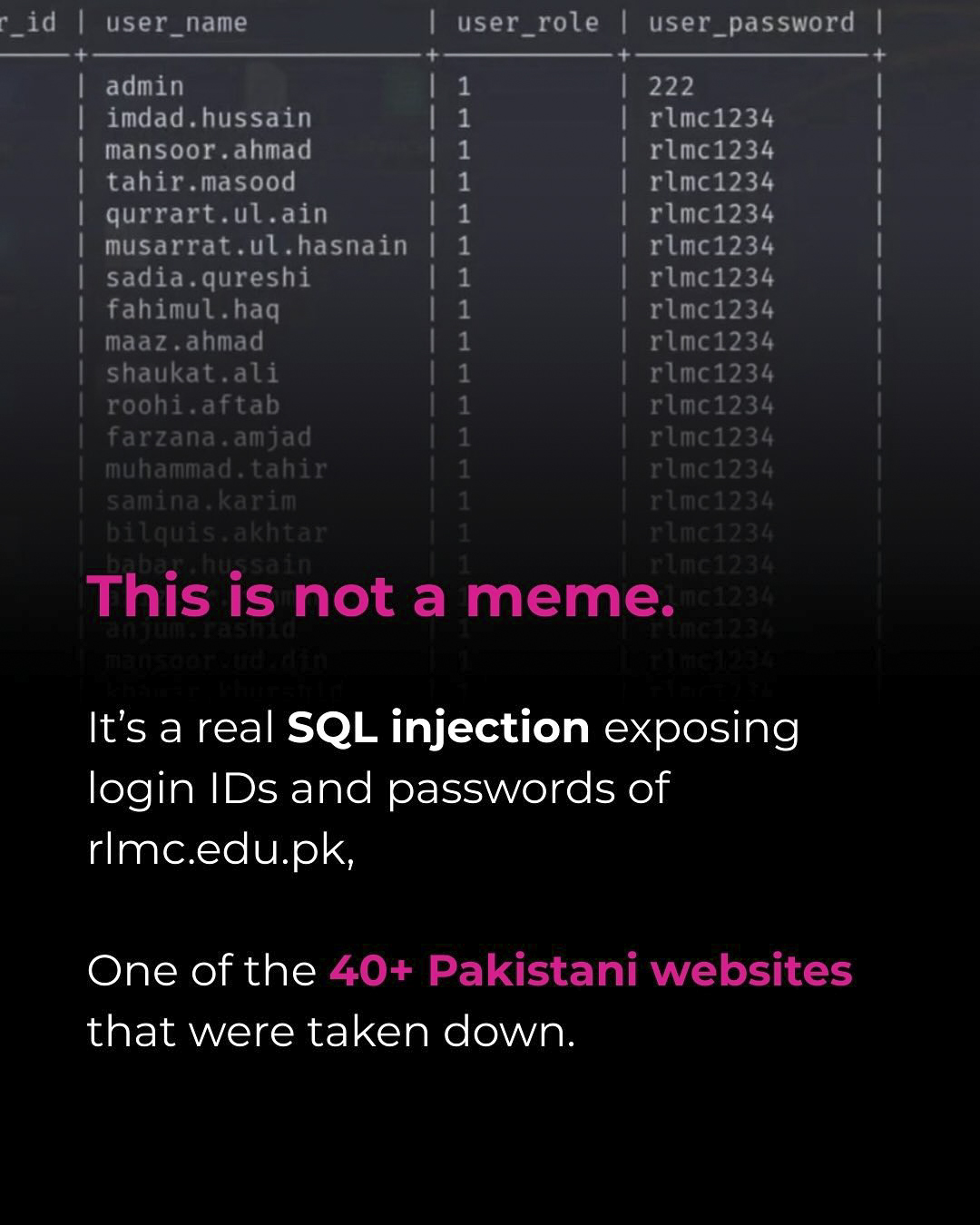
Security testing ensures that applications are free from vulnerabilities like SQL Injection, XSS, CSRF, and IDOR. SQL Injection occurs when unsanitized inputs allow attackers to manipulate database queries. This can be mitigated by using parameterized queries, preventing direct injection. XSS allows attackers to inject malicious scripts into web pages, and can be prevented by properly sanitizing or escaping user inputs. CSRF tricks users into executing unwanted actions; using CSRF tokens helps verify request authenticity. IDOR allows unauthorized access to data by manipulating object references, which can be avoided by implementing proper authorization checks. By integrating these security measures, you can safeguard your application from common attacks.
More like this
Recommendations from Medial
Vansh Khandelwal
Full Stack Web Devel... • 7m
In the rapidly evolving digital landscape, APIs (Application Programming Interfaces) serve as essential connectors among software applications, enabling seamless communication between systems. However, their accessibility also makes them prime target
See MoreAnsh Sarkar
Software, Physics, P... • 11m
I’ve been diving deep into voice agents, and it’s been an exciting challenge. Automating conversations isn’t just about speech recognition but rather about understanding intent, handling ambiguity, and making interactions feel natural. Trust me that
See MoreDownload the medial app to read full posts, comements and news.















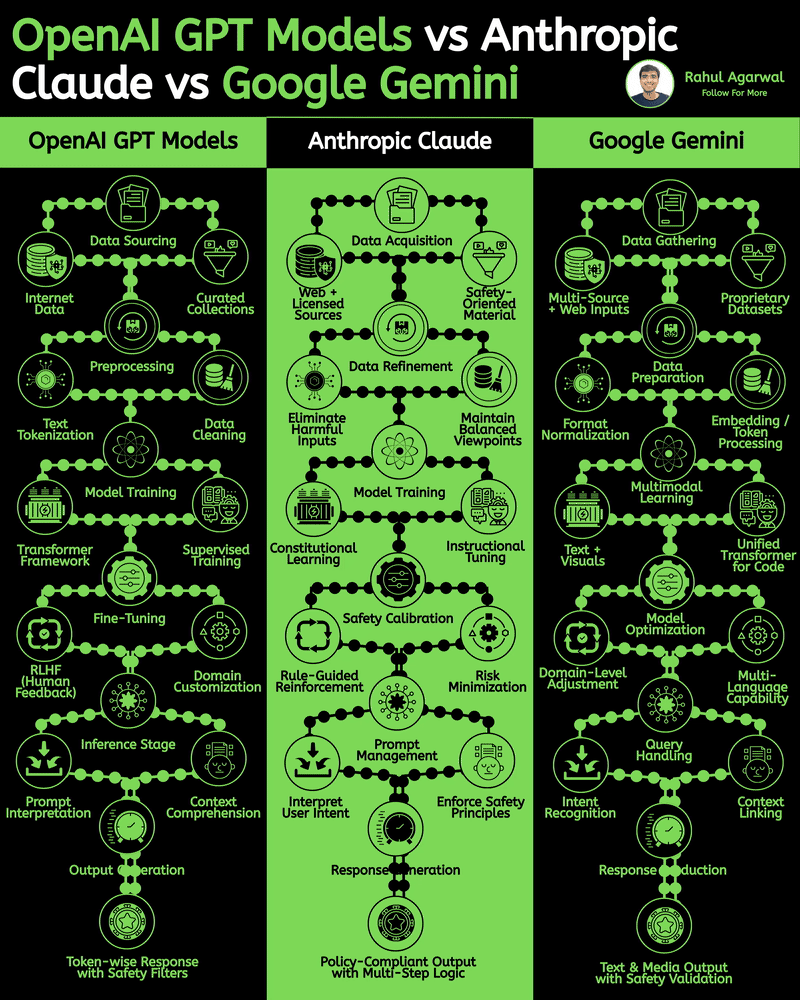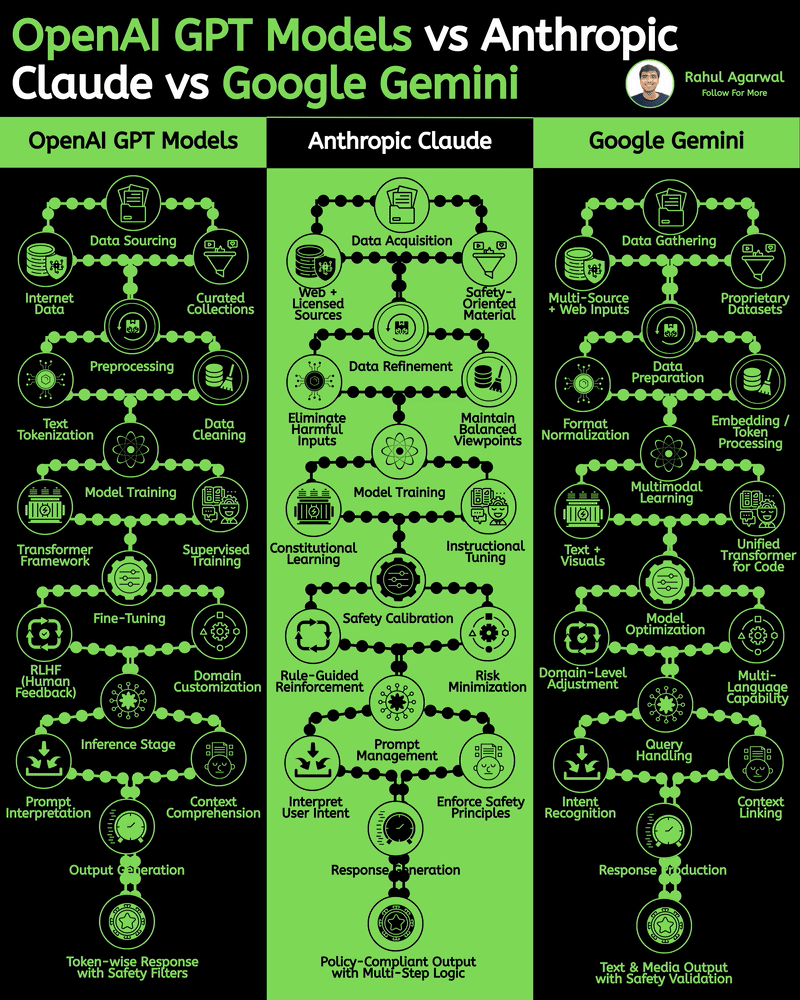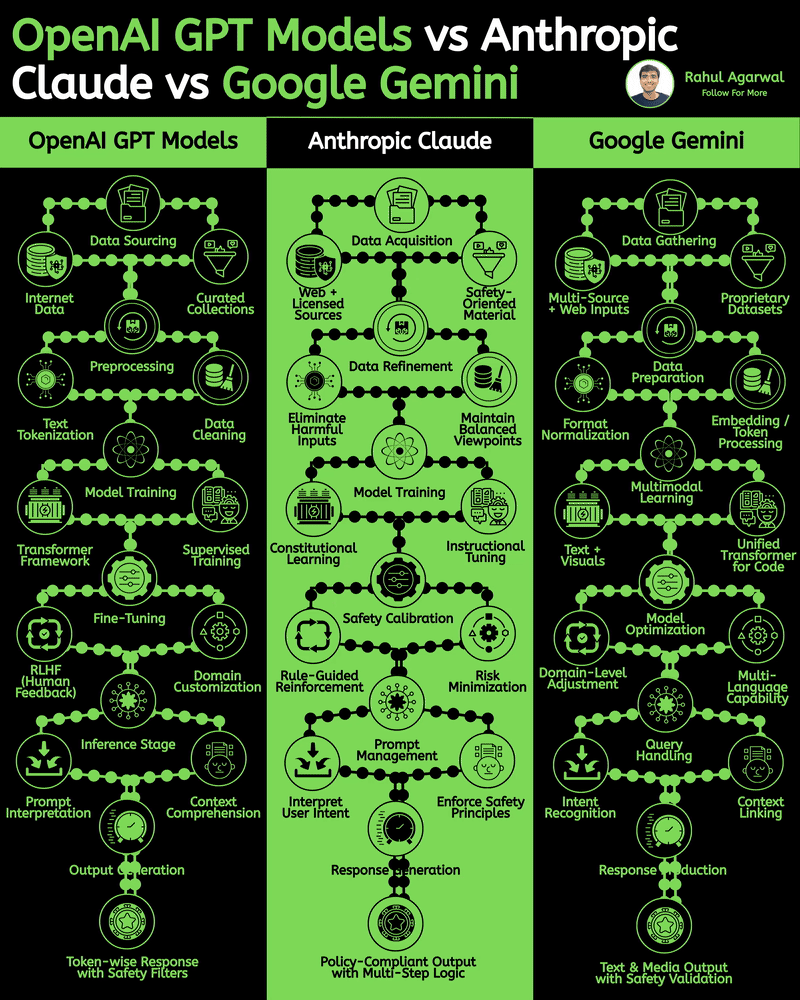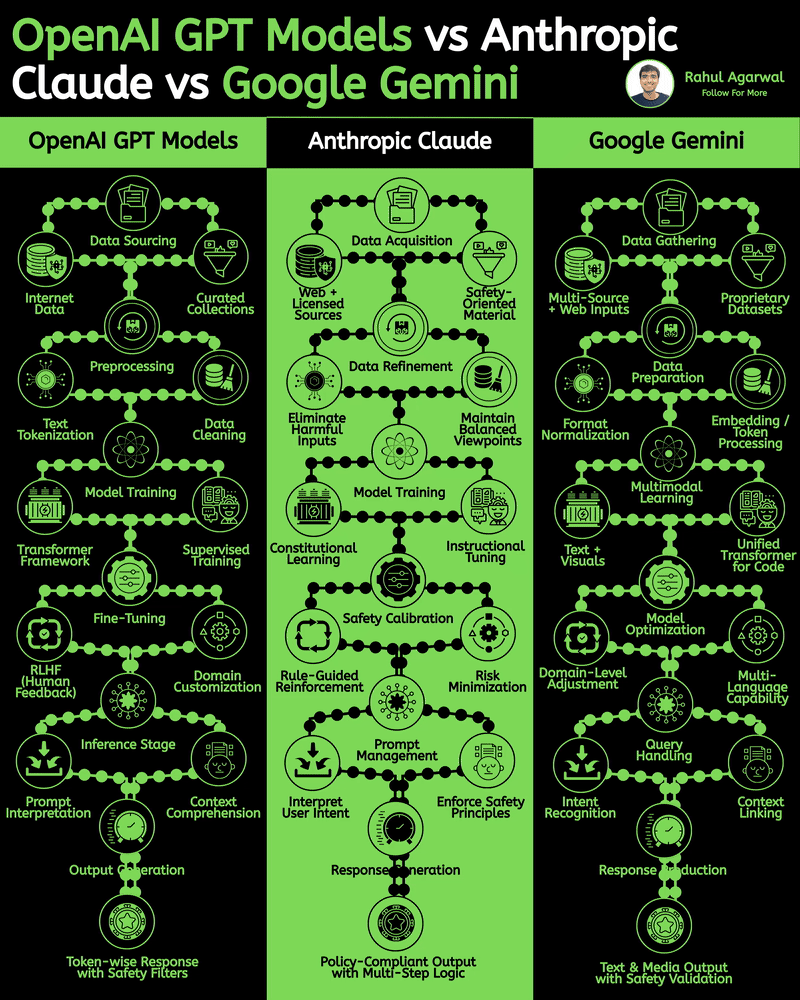
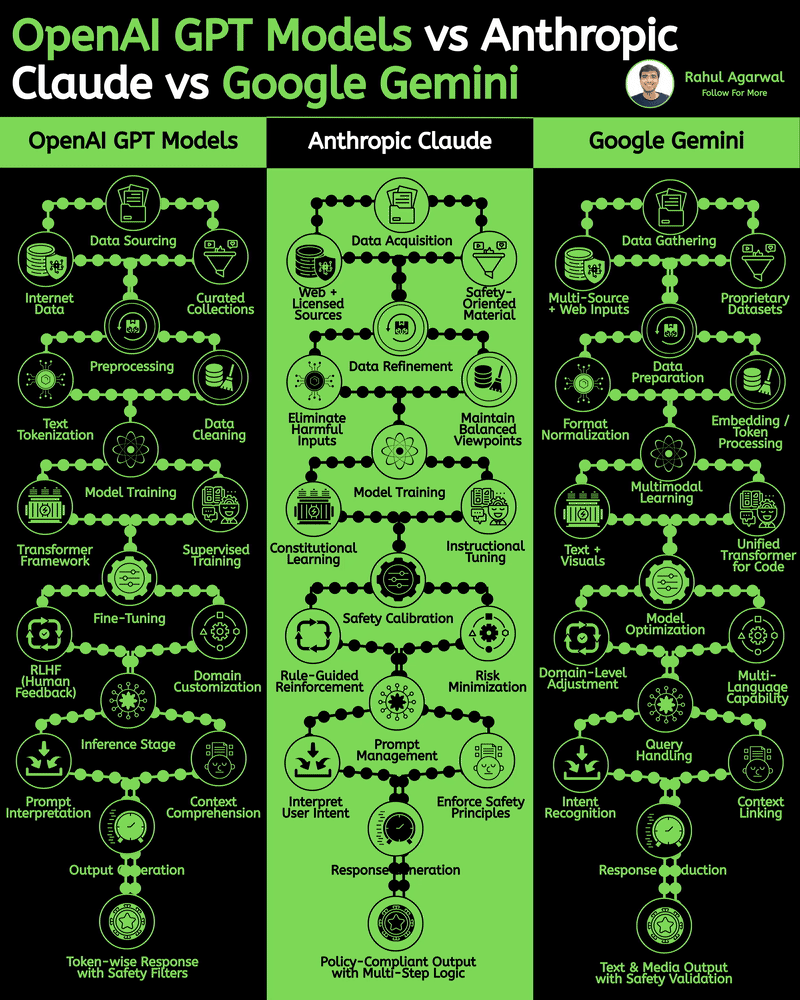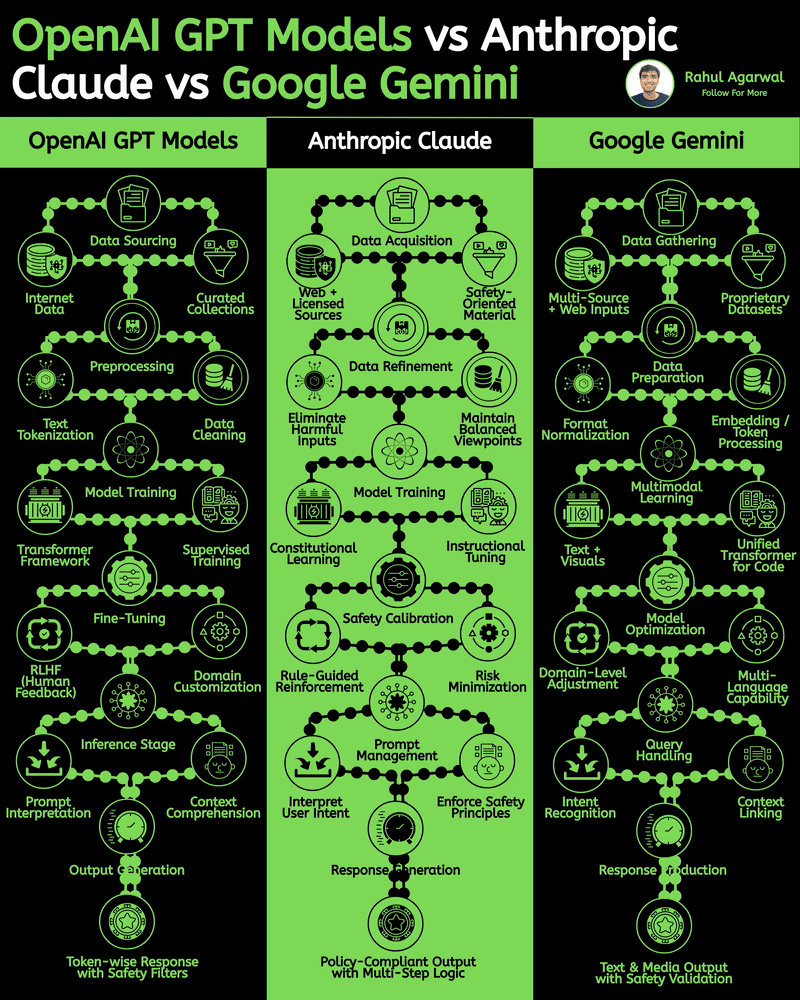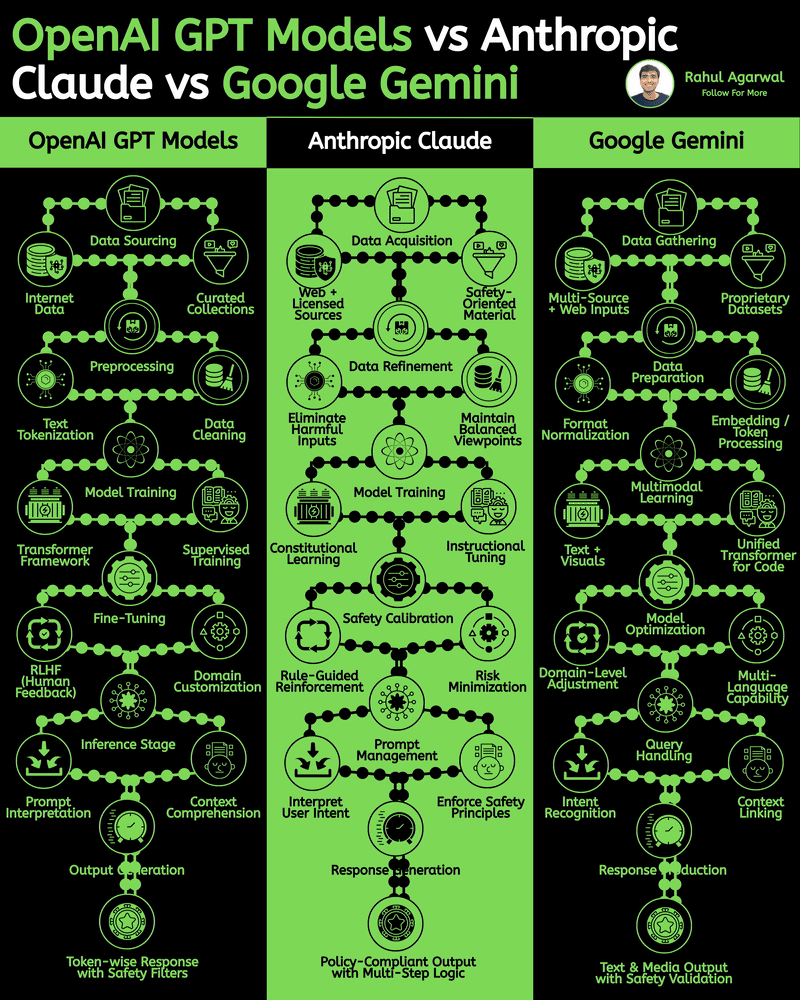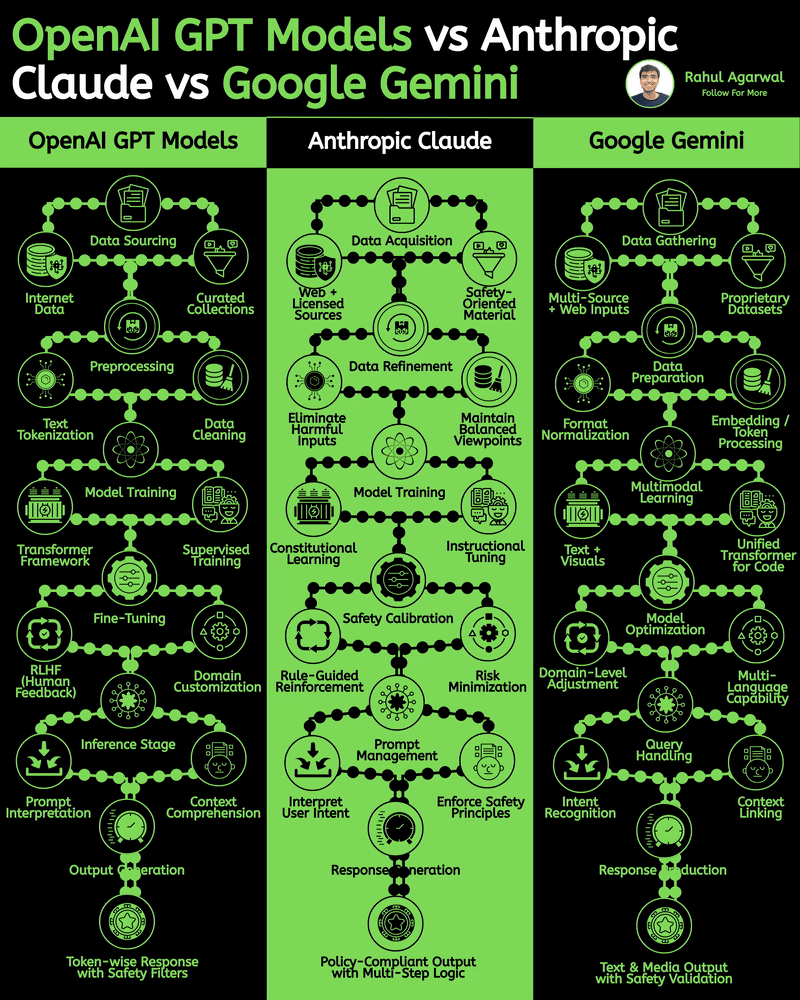

/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)



















