Back
More like this
Recommendations from Medial
Deekshith Korivi
Open to work at good... • 3m
i did use some of google ai feature such as visual representations where when ask for topic in now chart it gives us plane text but in this it gives us how we see it it break down part make it separate make them yhw slides view just try for be
See More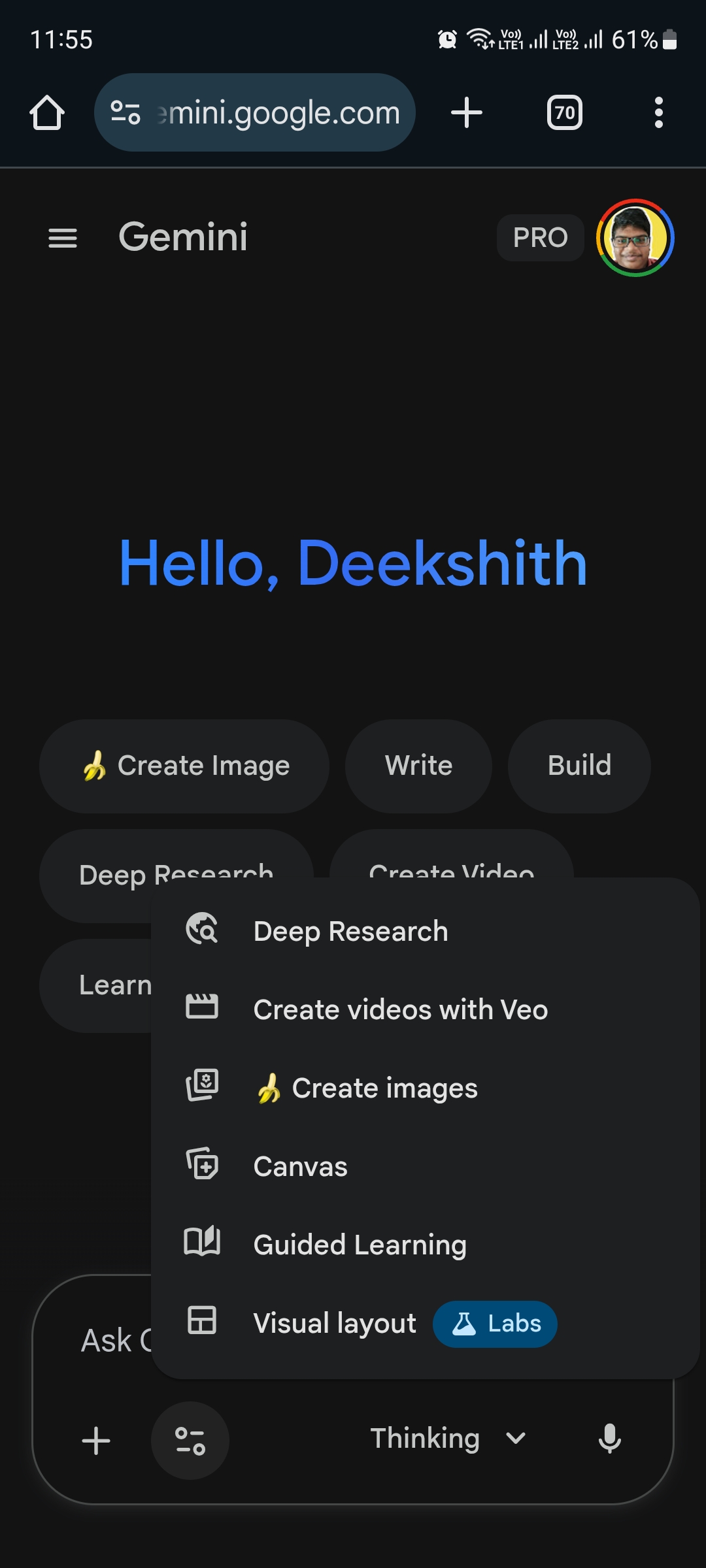
Amitash M S
Software Engineer | ... • 1y
Let's say you're commuting and you don't have a lot of time but you want to watch something. What about a platform which gives you byte sized entertainment? Maybe a horror or thriller short video of 10 mins or so. Maybe even a comedy show? Do you thi
See MoreVasvi Seth
Cyber Security Stude... • 1y
🔒 Understanding ZeroLogon: Microsoft's Netlogon Vulnerability 🔒 ZeroLogon, a critical vulnerability in Microsoft’s Netlogon authentication protocol, underscores the vital importance of robust cybersecurity measures. An authentication protocol ser
See MoreVasvi Seth
Cyber Security Stude... • 1y
Understanding Network Protocols: The Backbone of Digital Communication In the world of networking, protocols are crucial. A network protocol is essentially a set of rules used by two or more devices on a network to dictate the delivery and structure
See MoreDownload the medial app to read full posts, comements and news.



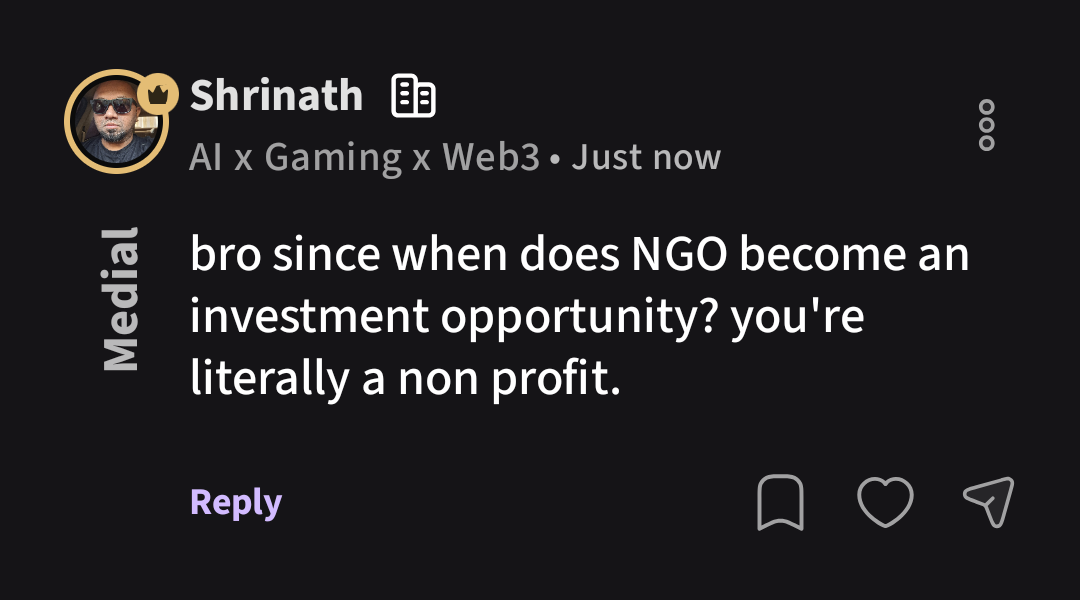








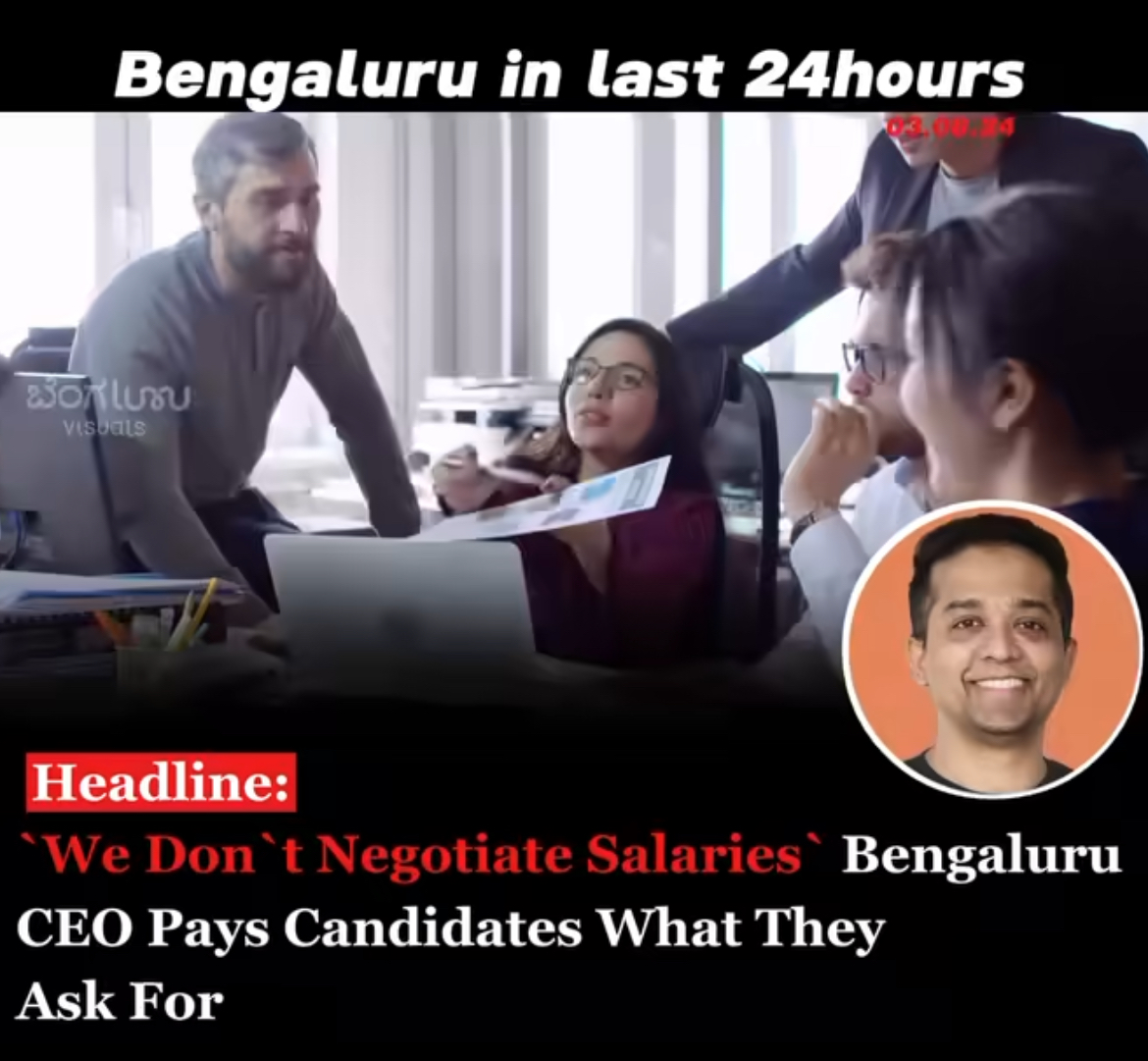


/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)




















