Back
Sheikh Ayan
Founder of VistaSec:... • 11m
🔐 Cybersecurity Tip: Protect Your Online Accounts! 🔐 Want to keep hackers out? Follow these steps: ✅ Enable 2FA – Use an authenticator app for extra security. ✅ Use Strong Passwords – Mix uppercase, lowercase, numbers & symbols. ✅ Beware of Phishing – Don’t click suspicious links or emails. ✅ Keep Software Updated – Patch vulnerabilities regularly. ✅ Use a VPN on Public Wi-Fi – Stay private & encrypted.
More like this
Recommendations from Medial
Mohammad Ali Shah
Co Founder & CEO at ... • 7m
🚨 Alert: 16 Billion Credentials Leaked-Is Your Account at Risk? A massive leak has exposed 16 billion credentials from past data breaches – including accounts from Gmail, Facebook, Instagram, Apple & more. 📰 Source: https://timesofindia.indiatime
See MoreKaran Jot Singh
Jack of all trades, ... • 7m
Week 1 wrap 🔥 ✅Wallet import/send $SOL ✅Balance + 2FA UI ✅NFT module WIP ✅2 awesome designers onboarded Gained the following metrics on x: 💯 Tweets • Followers • Following First post with 500+ views🚀 & Got the blue tick this week Let’s keep build
See MoreSourav Mishra
•
Codestam Technologies • 7m
guys, take 30 seconds and do this. seriously. go to 👉 https://haveibeenpwned.com type your email. and check if your data has been leaked in any breach. you’ll be surprised how often it happens — even from big platforms. why this matters: – your p
See More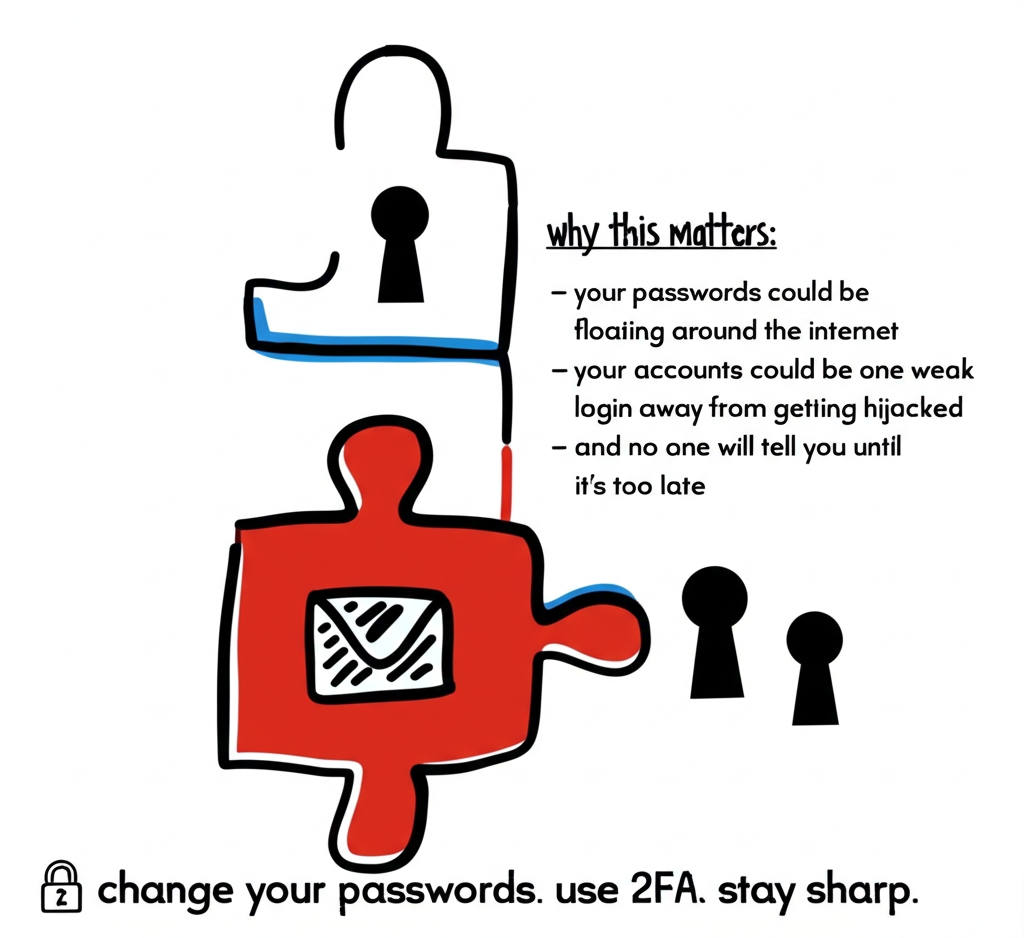
Sheikh Ayan
Founder of VistaSec:... • 10m
🔍 Top Log Monitoring Tools for Cybersecurity 🔍 Protecting your digital assets starts with real-time log monitoring! Here are the top log monitoring tools every cybersecurity professional should know: ✅ Splunk – Advanced analytics, real-time monit
See MoreSheikh Ayan
Founder of VistaSec:... • 10m
🔒 How to Secure Your System & Servers Like a Pro! 🚀 Follow these advanced tips to safeguard your systems and servers from potential attacks: ✅ Enable Multi-Factor Authentication (MFA) – Add an extra layer of security beyond passwords. 🛡 Implemen
See MoreAccount Deleted
•
Urmila Info Solution • 6m
The most addictive apps in the world aren’t lucky. They’re gamified. What do Duolingo, Fitbit & Notion have in common? 🎯 They use gamification to keep users hooked. 🎨 Their design rewards progress. ⚙️ Their logic feels natural. At Opslify, we he
See MoreDownload the medial app to read full posts, comements and news.































