Back
Shuvodip Ray
Never compromise wit... • 11m
⭐ The Domino Effect of a Single Breach 🔐 Imagine you use the same password for a social media account, email, and online banking. If hackers breach the social media platform (which happens daily), they’ll extract your credentials and test them on other sites. This automated process, called credential stuffing, often takes seconds. Suddenly, your email is compromised. From there, attackers can: -Reset passwords for your bank or other critical accounts. -Access sensitive emails containing tax documents or medical records. -Exploit saved payment details for fraudulent purchases. // For example, in 2022, a breach at ROCKSTAR GAMES exposed millions of passwords. Hackers used these credentials to drain bank accounts of users who reused passwords for PayPal or banking apps. 🛑The Numbers Don’t Lie🛑 -53% of people admit to reusing passwords. -Credential stuffing accounts for 34% of all login attempts on retail sites. -Stolen passwords sell for as little as $2 on the dark web, making reuse a goldmine for hackers. 🔐 How to Protect Yourself: + Use a password manager to generate and store unique, complex passwords. + Enable two-factor authentication for critical accounts. + Regularly check if your passwords are exposed via tools like Have I Been Pwned. Breaking the password reuse habit isn’t just about convenience—it’s about closing the door on cascading breaches that can devastate your digital life. Every unique password is a dead end for hackers

More like this
Recommendations from Medial
Mohammad Ali Shah
Co Founder & CEO at ... • 8m
🚨 Alert: 16 Billion Credentials Leaked-Is Your Account at Risk? A massive leak has exposed 16 billion credentials from past data breaches – including accounts from Gmail, Facebook, Instagram, Apple & more. 📰 Source: https://timesofindia.indiatime
See MoreSheikh Ayan
Founder of VistaSec:... • 11m
🔐 Cybersecurity Tip: Protect Your Online Accounts! 🔐 Want to keep hackers out? Follow these steps: ✅ Enable 2FA – Use an authenticator app for extra security. ✅ Use Strong Passwords – Mix uppercase, lowercase, numbers & symbols. ✅ Beware of Phish
See MoreAccount Deleted
Hey I am on Medial • 1y
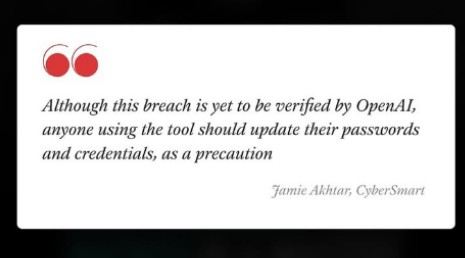
A report from The Information states that a hacker claims to have stolen login credentials— including emails and passwords— for 20 million OpenAI accounts and is selling them on the dark web. OpenAI is investigating the matter but maintains that the
See More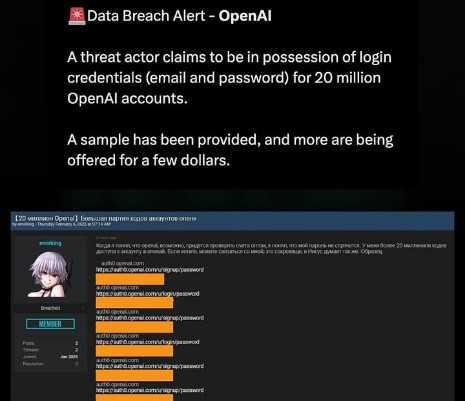
Mohd Rihan
Student| Passionate ... • 8m
Massive Data Leak Alert: Over 16 billion credentials (usernames & passwords) have been leaked online via logs from infostealer malware like RedLine & Raccoon. These include accounts from Google, Facebook, Apple, and more. Most data is fresh, posing h
See MoreShuvodip Ray
Never compromise wit... • 10m
🛡️ Using the same password everywhere is a big mistake! Let’s say you use 'Raju123' for Netflix and Gmail. A hacker gets it from Netflix—maybe with a tool like Hydra, which guesses passwords fast. They check your Netflix profile, see your Gmail ID
See More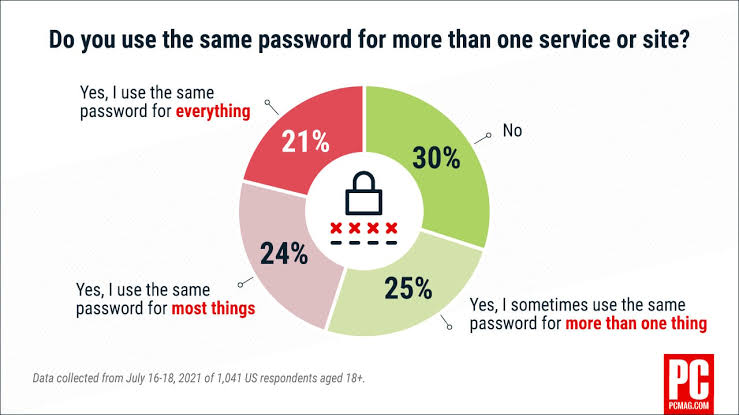
Sourav Mishra
•
Codestam Technologies • 8m
guys, take 30 seconds and do this. seriously. go to 👉 https://haveibeenpwned.com type your email. and check if your data has been leaked in any breach. you’ll be surprised how often it happens — even from big platforms. why this matters: – your p
See More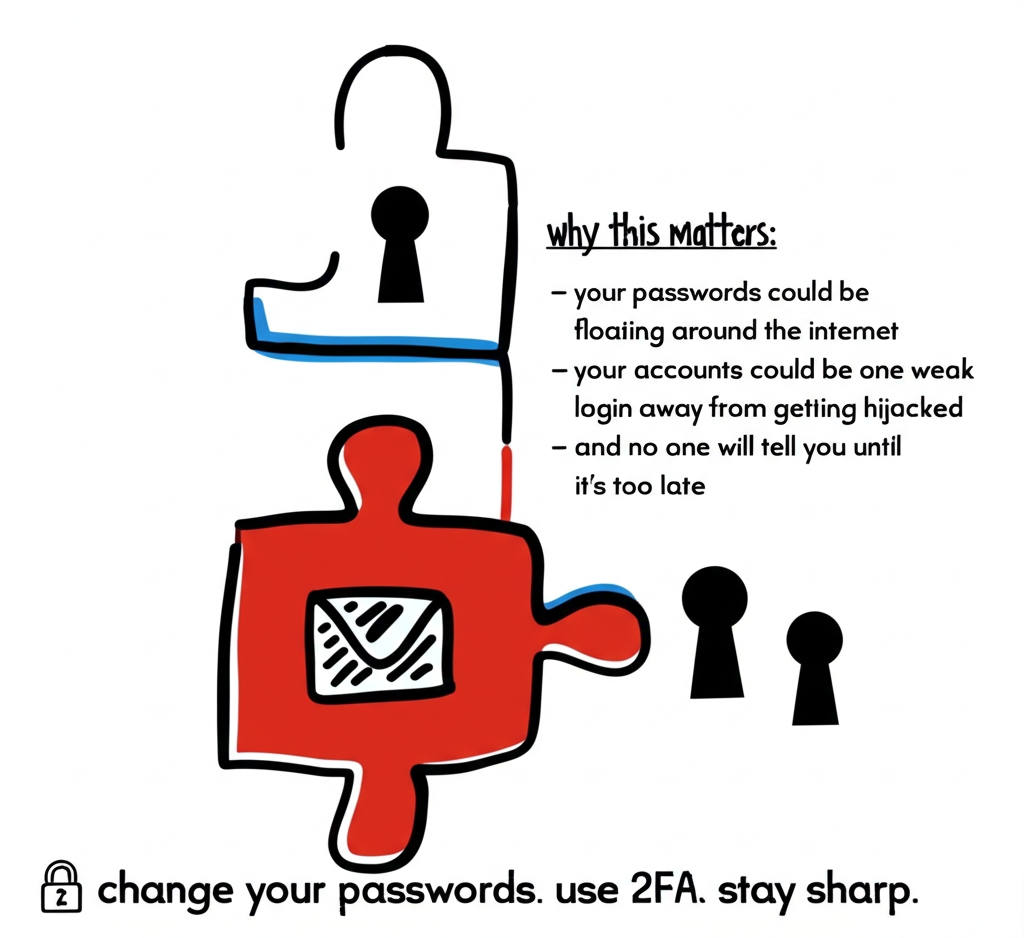
Download the medial app to read full posts, comements and news.















/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)




















