Back
Vasvi Seth
Cyber Security Stude... • 1y
🔒 ProxyLogon: Addressing a Critical Vulnerability in Microsoft Exchange Server 🔒 Attention cybersecurity professionals! 🚨 ProxyLogon is not just another vulnerability—it's a critical pre-authenticated threat affecting Microsoft Exchange Server. This flaw enables threat actors to bypass authentication processes, paving the way for deploying malicious code remotely. Stay vigilant and ensure your systems are fortified against ProxyLogon and other emerging threats. Let's prioritize cybersecurity to safeguard our digital infrastructure. 💻
More like this
Recommendations from Medial
Vasvi Seth
Cyber Security Stude... • 1y
Ensuring robust cybersecurity measures is essential in today's digital landscape. Are you familiar with Server-Side Request Forgery (SSRF)? This vulnerability can enable attackers to manipulate server-side applications, granting unauthorized acces
See MoreVasvi Seth
Cyber Security Stude... • 1y
🔒 Understanding ZeroLogon: Microsoft's Netlogon Vulnerability 🔒 ZeroLogon, a critical vulnerability in Microsoft’s Netlogon authentication protocol, underscores the vital importance of robust cybersecurity measures. An authentication protocol ser
See MoreVenkatesh
Bussiness Developmen... • 1y
🚨 Exciting Opportunity Alert! 🚨 We are seeking a skilled Vulnerability and Penetration Tester for a critical project with the Ministry of Finance. If you're passionate about cybersecurity and ensuring the safety of critical systems, this role is a
See More
Vasvi Seth
Cyber Security Stude... • 1y
💼 Understanding Risks in Cybersecurity 💼 Risks are the backbone of cybersecurity strategy – they're what we guard against, mitigate, and manage every day. But what exactly is a risk? 🔒 A risk is anything that can affect the confidentiality, inte
See MoreTarun Patel
Cybersecurity Analys... • 1y
Invest in the Future of Cybersecurity with Us! 🔒 Join Us in Building India’s Leading Cybersecurity Ecosystem We are launching an innovative cybersecurity company in India, offering: ✅ Cutting-Edge Cybersecurity Products – Devices like Flipper Zero
See MoreKunal Salekar
Hey I am on Medial • 7m
In the Age of AI, the Cybersecurity Threat is Evolving Faster Than Ever 🚨 In yet another alarming wake-up call for the digital economy, CoinDCX one of India’s prominent cryptocurrency exchanges, has reportedly suffered a massive security breach, lo
See More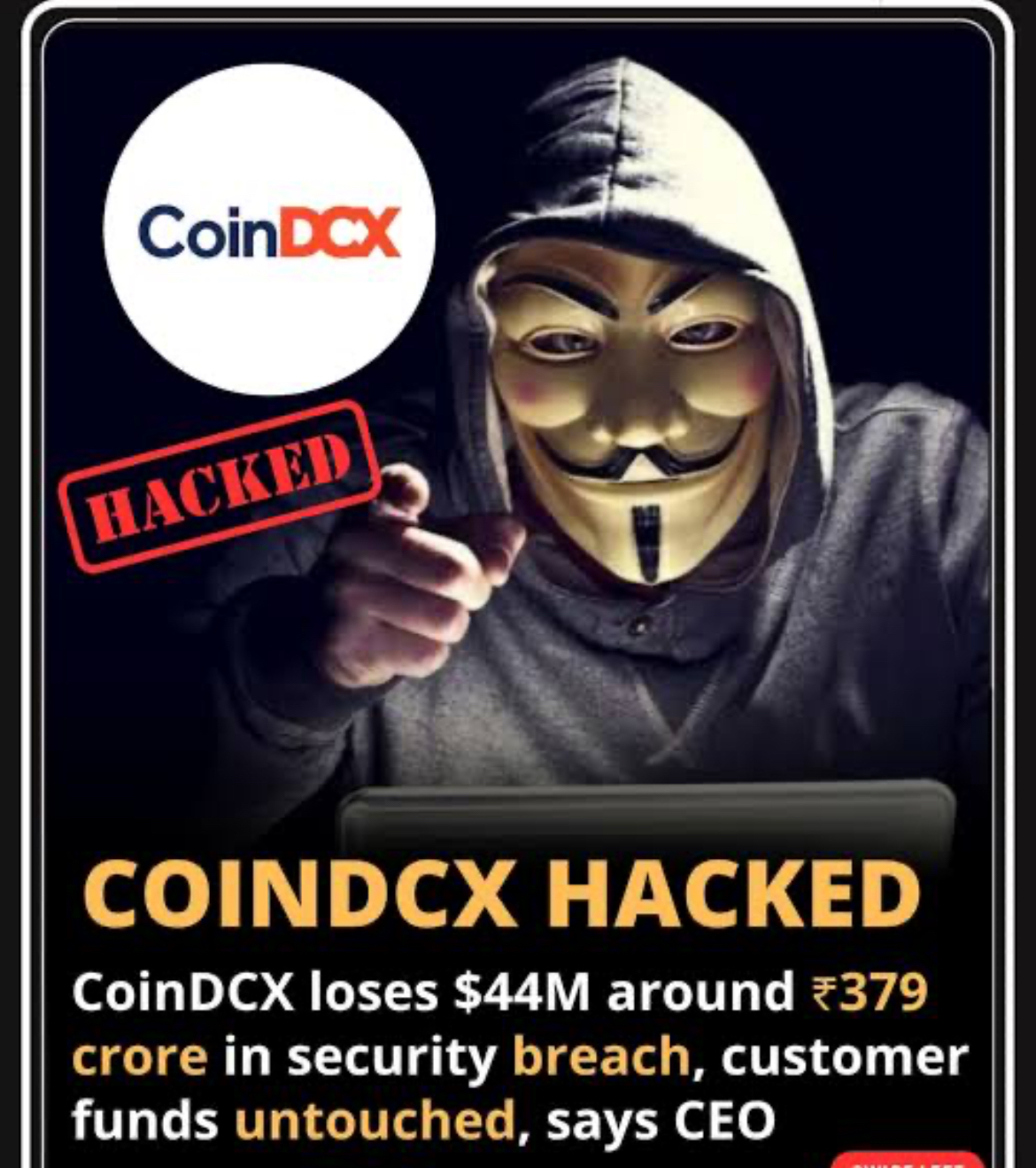
Download the medial app to read full posts, comements and news.









/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)





















