Back
Esther Sarabia
Hey I am on Medial • 10d
How TECHY FORCE CYBER RETRIEVAL (TFCR) Makes Crypto Recovery Possible—Even When It Seems Hopeless The promise of cryptocurrency is powerful: financial sovereignty, borderless transactions, and decentralized control. But with that freedom comes risk. Scammers have grown increasingly sophisticated—impersonating support agents, deploying fake investment apps, exploiting smart contract vulnerabilities, and launching phishing campaigns that even tech-savvy users fall for. Once funds are sent, many victims assume they’re gone forever. CONTACT US HERE WhatsApp +.1.5.6.1.7.2.6.3.6.9.7 Telegram +.15.6.1.7.2.6.3.6.9.7 At TECHY FORCE CYBER RETRIEVAL (TFCR), we know better. Because recovery is possible—and we’ve proven it again and again. Our Proven Process: Precision, Ethics, and Results Since our founding, TFCR has operated at the intersection of **ethical hacking, digital forensics, and regulatory compliance**. We’re not just a recovery service—we’re a federally recognized cybersecurity firm and a Google-certified business, held to the highest standards of transparency and accountability. Here’s how we work: 1. Immediate Case Assessment – No Upfront Fees When you contact us, our certified analysts conduct a free, confidential review of your incident. We verify transaction hashes, wallet addresses, and attack vectors—without asking for payment or private keys. If your case is viable, we move forward on a **success-based model**: you pay only if we recover your assets. 2. Advanced Blockchain Forensics Using proprietary tools and partnerships with global blockchain intelligence platforms, our team traces stolen funds across chains—even through mixers, bridges, and privacy protocols. In 2025 alone, this approach helped us track and intercept assets across Ethereum, Bitcoin, Solana, and Binance Smart Chain. 3. Strategic Coordination with Exchanges & Authorities As a federally recognized entity, TFCR can legally engage with KYC-compliant exchanges, custodians, and law enforcement. When stolen crypto lands in a regulated wallet, we initiate freeze requests and asset preservation protocols—something individual victims cannot do on their own. 4. Secure Asset Return Once recovered, funds are returned directly to a new, secure wallet under your control. We never hold client assets long-term and provide full audit trails for every transaction.

More like this
Recommendations from Medial
Vasvi Seth
Cyber Security Stude... • 1y
Decoding Network Protocols: Communication, Management, and Security Network protocols are the backbone of our digital world, enabling seamless communication between devices. These protocols can be broadly categorized into three main types: communica
See MoreTushar Aher Patil
Trying to do better • 1y
Day 6 About Basic Finance and Accounting Concepts Here's Some New Concepts 3. Tangible Assets Physical assets that have a physical form and can be touched. Examples: machinery, real estate, vehicles, inventory, and office supplies. 4. Intangibl
See More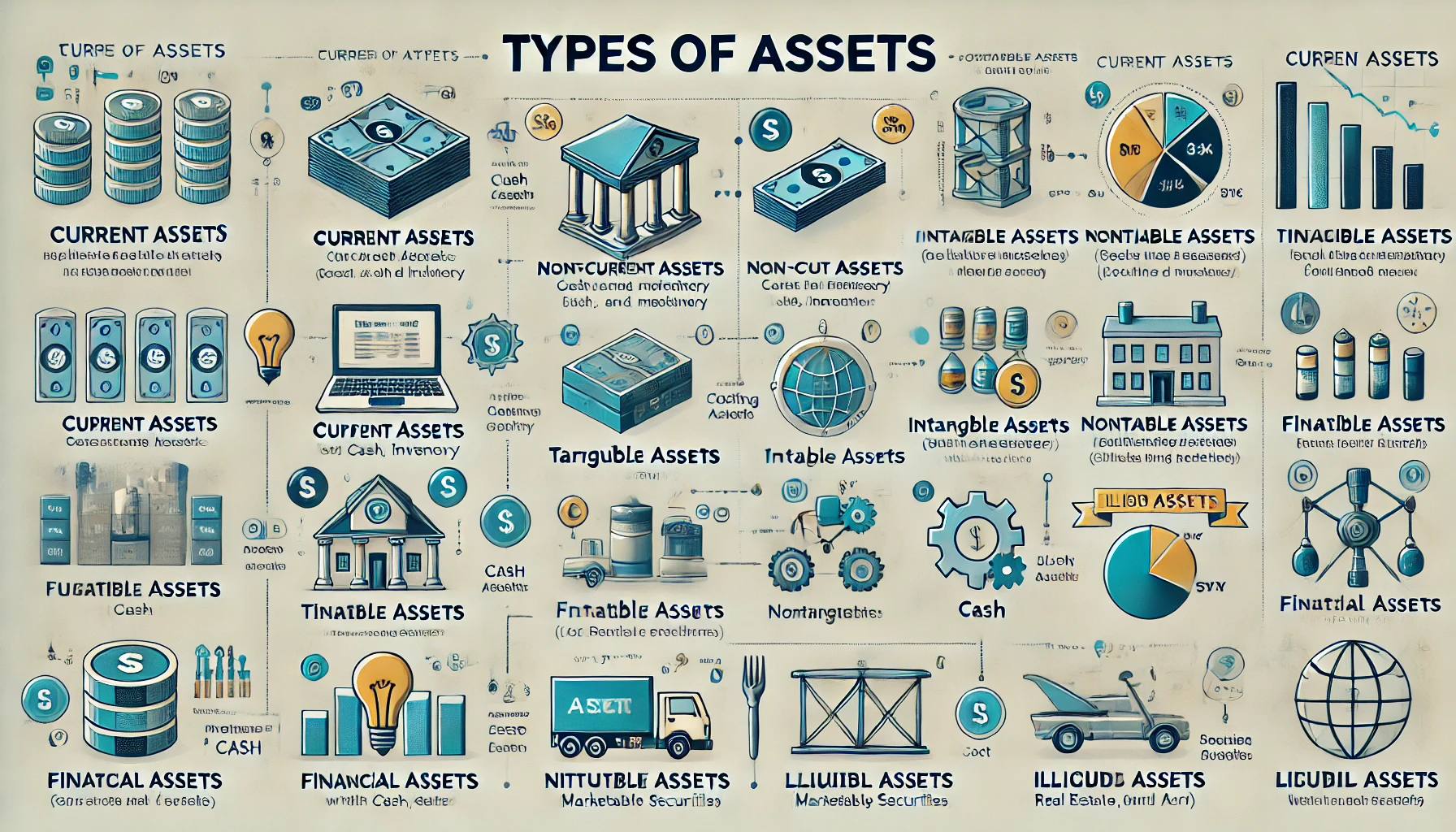
Download the medial app to read full posts, comements and news.











/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)




















