Back
Vasvi Seth
Cyber Security Stude... • 1y
Decoding Network Protocols: Communication, Management, and Security Network protocols are the backbone of our digital world, enabling seamless communication between devices. These protocols can be broadly categorized into three main types: communication protocols, management protocols, and security protocols. Each type plays a vital role in ensuring data is transmitted efficiently and securely. While there are dozens of different network protocols, it’s not necessary to memorize all of them, especially if you're just starting out as a security analyst. However, having a solid understanding of the key protocols outlined in this reading is essential. These protocols will form the foundation of your knowledge and help you navigate the complexities of network communication and security.
More like this
Recommendations from Medial
Vasvi Seth
Cyber Security Stude... • 1y
Delving into Communication Protocols: The Pillars of Network Transmission Communication protocols are fundamental to the exchange of information across networks. They govern how data is transmitted between devices, ensuring that communication is eff
See MoreVasvi Seth
Cyber Security Stude... • 1y
Understanding Network Protocols: The Backbone of Digital Communication In the world of networking, protocols are crucial. A network protocol is essentially a set of rules used by two or more devices on a network to dictate the delivery and structure
See MoreSandeep Jangir
Cyber Security Profe... • 1y
I'm looking for a co-founder for the Cyber Security Start-up. Anybody interested can ping me. I'm looking for who is good at communication skills, management skills, and technical skills. this startup is based on cyber security training and services
See MoreSheikh Ayan
Founder of VistaSec:... • 1y
🚨 Top IoT Vulnerabilities You Need to Know! 🚨 🔹 Weak Passwords & Default Credentials – Many IoT devices ship with default passwords that are easy to guess. 🔹 Unpatched Firmware – Outdated software can have security flaws that hackers exploit. 🔹
See MoreVasvi Seth
Cyber Security Stude... • 1y
Exploring Communication Protocols: Transmission Control Protocol (TCP) Communication protocols are the cornerstone of network transmission, dictating how data is exchanged between devices. They ensure efficient and reliable communication, including
See MoreRosy
# Digital Marketing ... • 1y
Media strategies can be broadly categorized into earned, owned, and paid media. Each type plays a unique role: earned media focuses on organic brand mentions, owned media includes content you control like your website or social profiles, and paid med
See More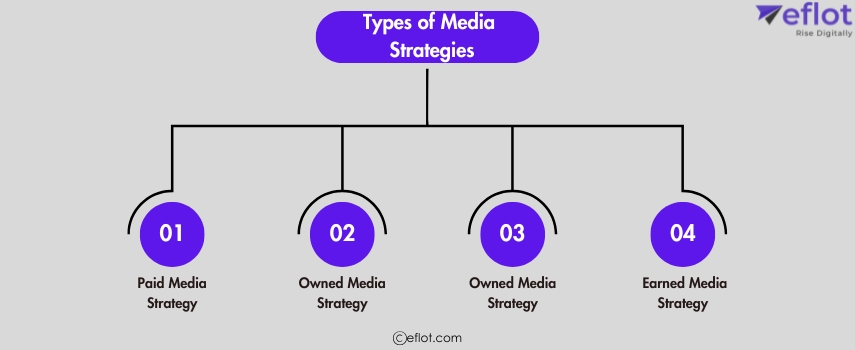
Sachin Jataw
Hey I am on Medial • 1y
Creating a self-sustaining network that operates independently of traditional cellular SIM cards or satellite connections is a revolutionary idea. Such a system has the potential to transform communication, enhance connectivity in remote areas, and p
See MoreDownload the medial app to read full posts, comements and news.










/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)




















