Back
Vivek Joshi
Director & CEO @ Exc... • 10m
Balancing Internal Excellence with External Vigilance In pursuing growth, our organization has remained committed to self-determined KPIs, internal benchmarking, and competing solely against our own standards of excellence. This approach has delivered authentic value creation and sustained innovation. However, a recent incident involving unethical competitor interference has highlighted the need for greater external awareness and risk management. While we continue to prioritize internal excellence, we are evolving our strategy to strengthen external intelligence and stakeholder engagement. True resilience requires more than internal strength — it demands proactive understanding of the environment in which we operate.

More like this
Recommendations from Medial
Parshya Bora
Founder @stealth • 1y
At Future4coding by Curiolab our newsletter, we're building the gold standard in AI-assisted Software intelligence. Our team has been dedicated to understanding and evaluating open-source LLMs in the coding world — benchmarking models, creating compa
See More
Abhishek S Kulkarni
Localpreneur | on a ... • 1y
Anybody working on creating a internal creative operations software for creative industry, example Advertising, Social Media, and other related fields. Idea is to make a tool where a monthly idea/content calendar is prepared and for particular date
See MoreRakesh Mishra
Everyone is doing go... • 1y
Shashwatam Eco-Chic Creation LLP: Officially Recognized Under Startup India! A proud moment for us! Shashwatam Eco-Chic Creation LLP has been officially recognized as a Startup by the Government of India under the Department for Promotion of Industr
See More
Vasvi Seth
Cyber Security Stude... • 1y
🔒 As an entry-level security analyst, safeguarding organizational assets against threats is paramount. Understanding the various forms of threats is key to fortifying our defenses. Here are two common types every analyst should be vigilant about: •
See MoreVasvi Seth
Cyber Security Stude... • 1y
Understanding the diverse landscape of cybersecurity threats is crucial in today's digital age. A threat actor, whether an individual or a group, can pose significant risks to the security of our systems and data. This risk encompasses various aspect
See MoreHEALTH BEYOND HEALING PVT LTD
Health begins after ... • 1y
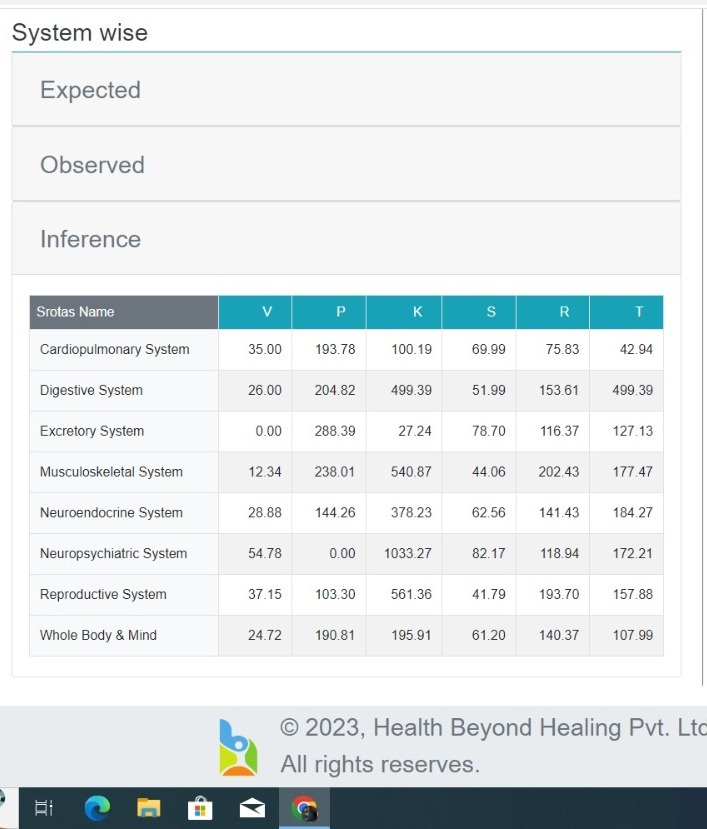
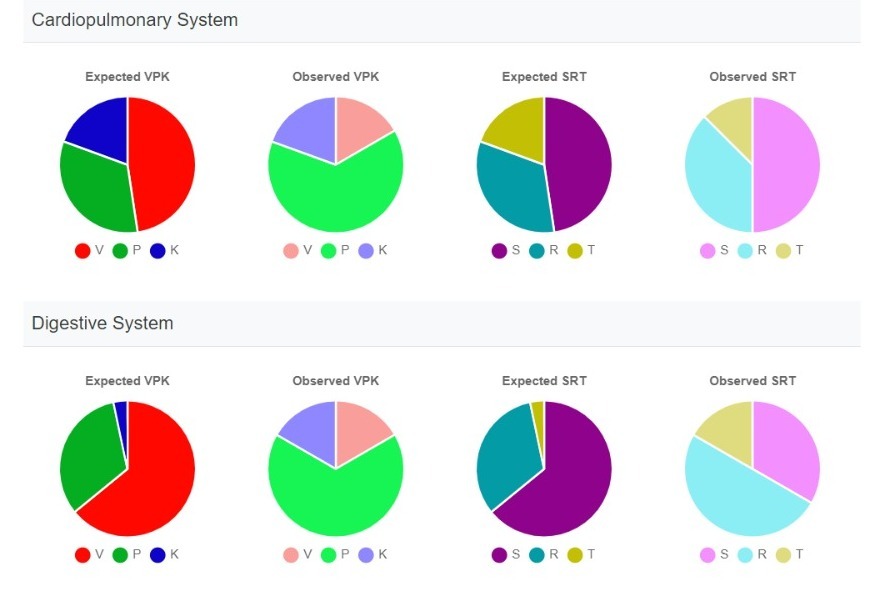
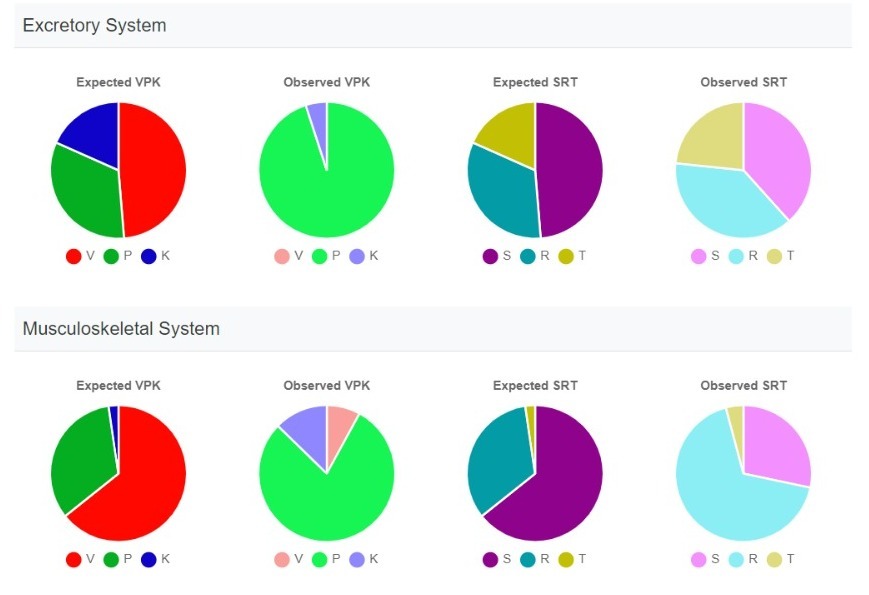
We are a 4-year-old Ayurveda research startup with collaborations with Ayurvedic Health Iceland Ehf. and VedamagT Ehf. in Iceland, driving Ayurveda education and healthcare globally. Our vision is encapsulated in "स्वस्थस्य स्वास्थ्य रक्षणम्" (Health
See More
Download the medial app to read full posts, comements and news.








/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)




















