Back
Sheikh Ayan
Founder of VistaSec:... • 10m
🔵 Advanced Blue Teaming Guide 🔵 🛡 1. Proactive Threat Hunting – Don’t wait for alerts. Use behavioral analysis and anomaly detection to identify hidden threats before they strike. 🕵️♂️ 2. Master Log Analysis – Collect and correlate logs from SIEMs (Splunk, ELK, Graylog) to detect subtle attack patterns and insider threats. 🔍 3. Leverage Threat Intelligence – Integrate CTI (CrowdStrike, MISP, VirusTotal) to anticipate attack trends and block malicious indicators in advance. 🚦 4. Enhance Endpoint Defense – Deploy EDR/XDR solutions (CrowdStrike, SentinelOne) and use YARA rules to detect malware variants in real time. 🛑 5. Zero Trust Architecture – Implement strict access controls (MFA, least privilege, network segmentation) to limit attacker movement. 💨 6. Rapid Incident Response – Build an IR playbook, automate containment with SOAR. 📊 7. Adversary Emulation – Use MITRE ATT&CK, Atomic Red Team, and Purple Teaming to test.
More like this
Recommendations from Medial
Arun George
Startup Enthusiast |... • 10m
Nebula iXDR replaces complex and expensive security infrastructure with a simple, subscription-based solution that’s easy to deploy, scale, and manage. Designed for scalability and speed, Nebula iXDR automates threat detection and response, enabling
See More
Sidhant Pandey
Software Developer f... • 5m
A "zero-day AI attack" means hackers using AI to exploit flaws before anyone even knows they exist. 🚨 Scary? Yes. But here's the good news -> the same AI power can also detect & fix those flaws in real-time, something humans could never do fast eno
See MoreSheikh Ayan
Founder of VistaSec:... • 7m
🔴 Red Teaming Tips & Tricks Red Teaming isn't just about hacking — it's about thinking like a threat actor and testing an organization’s detection, defense, and response capabilities. 🛠 1. Blend In with Normal Traffic Use tools like Cobalt Strike
See MoreSheikh Ayan
Founder of VistaSec:... • 11m
🚨 Critical Alert: Ransomware Attack on Ardent Health Services 🚨 In November 2023, Ardent Health Services fell victim to a ransomware attack, forcing the healthcare provider to take its network offline to contain the damage. This led to operational
See MoreSheikh Ayan
Founder of VistaSec:... • 10m
🚨 Ransomware Attack Recovery Plan: 8 Critical Steps to Restore & Secure Your Business! 🚨 A ransomware attack can be devastating, but swift action can help minimize damage. Follow these 8 essential steps to recover effectively: 1️⃣ Isolate Infecte
See MoreDownload the medial app to read full posts, comements and news.








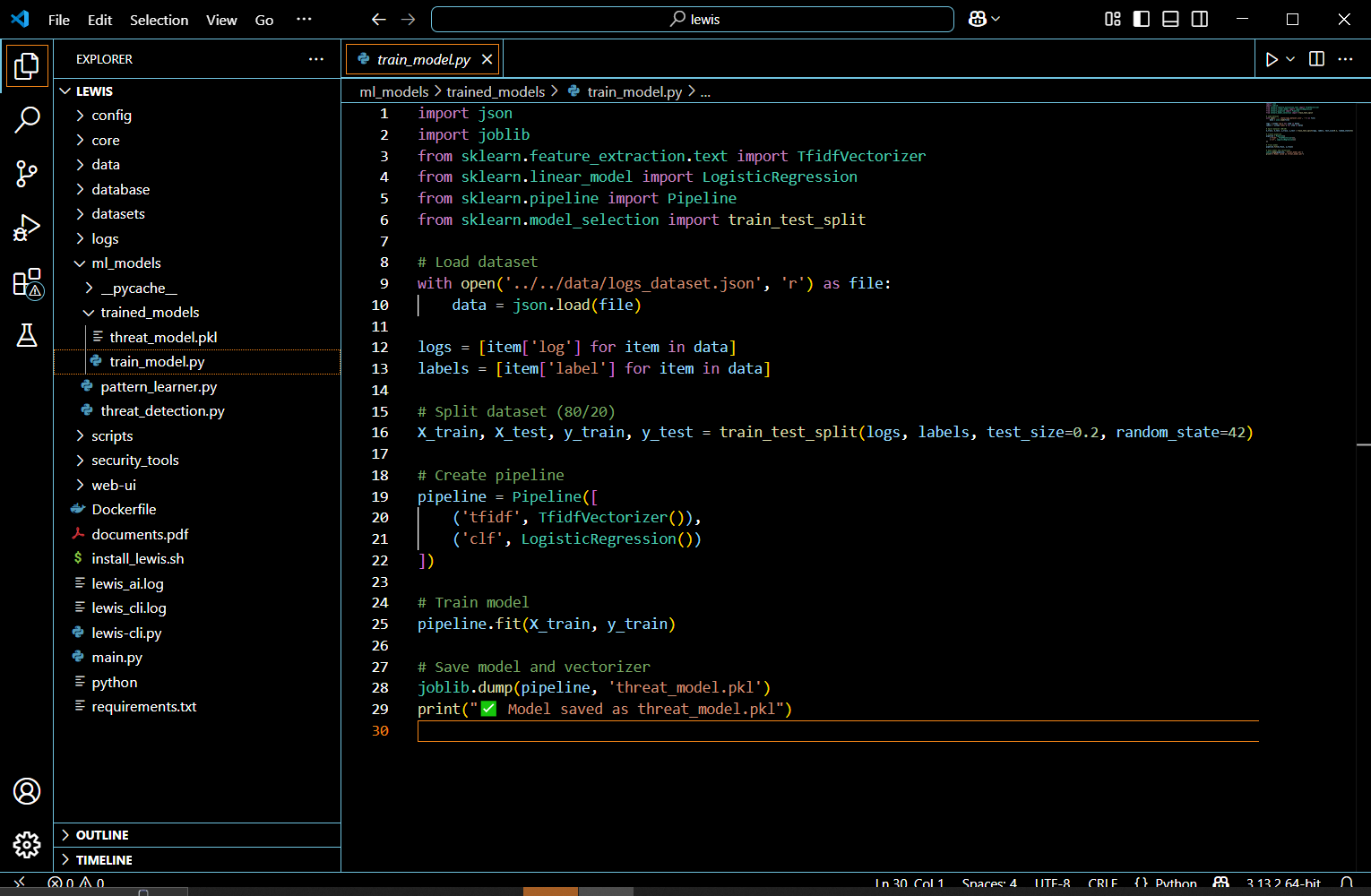
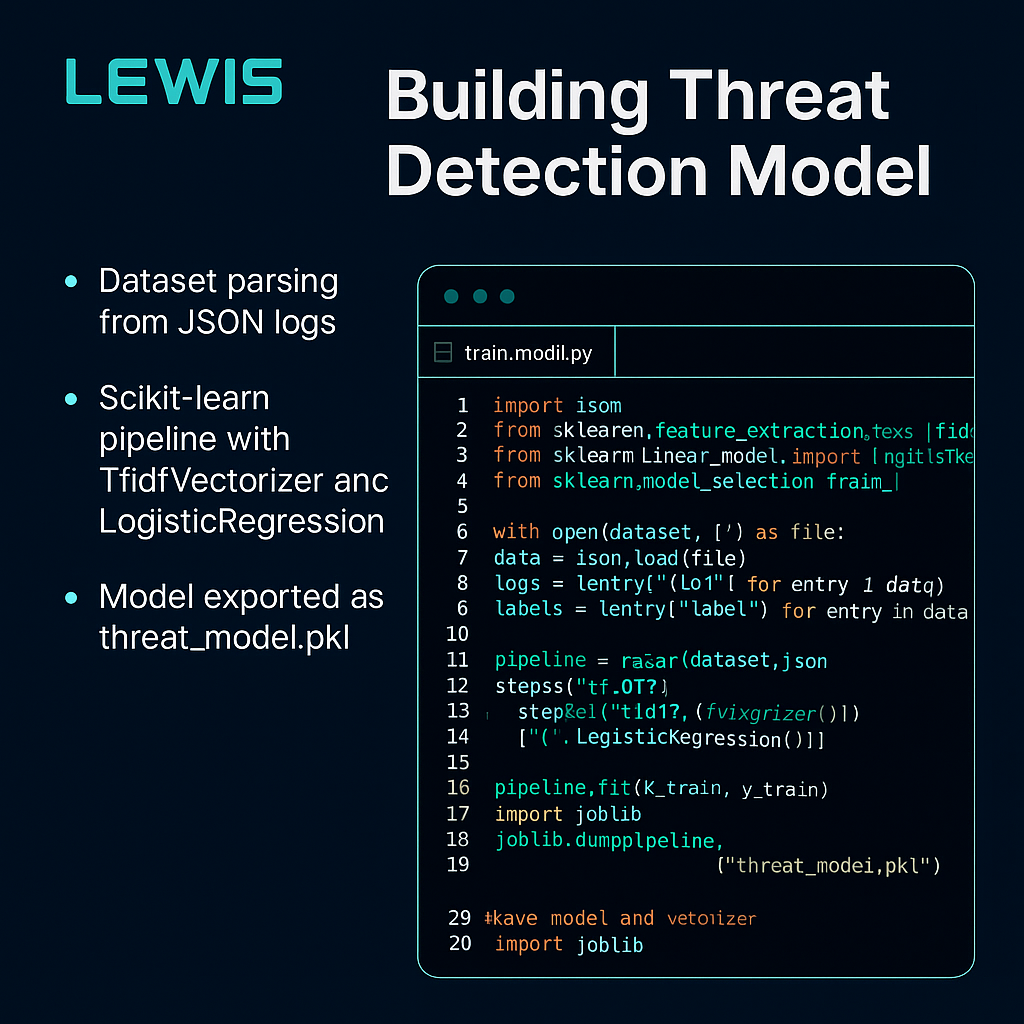

/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)





















