Back
Zain Abdullah
Cyber Security Analy... • 11m
To validate your product, it is essential to assess its market value and determine whether there is a demand for it. After developing a MVP, the next step is to conduct testing. If you have created an advanced enterprise-level file encryption software, how will you identify potential users/clients for testing?

More like this
Recommendations from Medial
Sheikh Ayan
Founder of VistaSec:... • 1y
🔥 Top Exploitation Tools for Penetration Testing 🔥 🔹 Metasploit Framework – The go-to tool for developing, testing, and executing exploits efficiently. 🔹 Cobalt Strike – Advanced red teaming tool for post-exploitation, persistence, and lateral
See Morefinancialnews
Founder And CEO Of F... • 1y
Indian Semiconductor Lab Provides Fab Services to Boost Startup Innovation India's SCL Offers Free Fab Support to Chip Design Startups India's first chip fabrication unit, Semi-Conductor Laboratory (SCL), Mohali, is set to provide comprehensive sup
See MoreSheikh Ayan
Founder of VistaSec:... • 6m
📖 What is White Box Penetration Testing? White Box Penetration Testing (also called Clear Box, Glass Box, or Transparent Box Testing) is a security testing approach where the tester is given full knowledge of the target system before the assessment
See MoreTarun Patel
Cybersecurity Analys... • 1y
Hiring Alert: Ethical Hacker Wanted! We are looking for a skilled Ethical Hacker to join our team at Selfsecure. If you're passionate about cybersecurity, penetration testing, and ethical hacking, this is your chance to work with a growing cybersecu
See MoreJewelpik App
House of jewellery b... • 1y
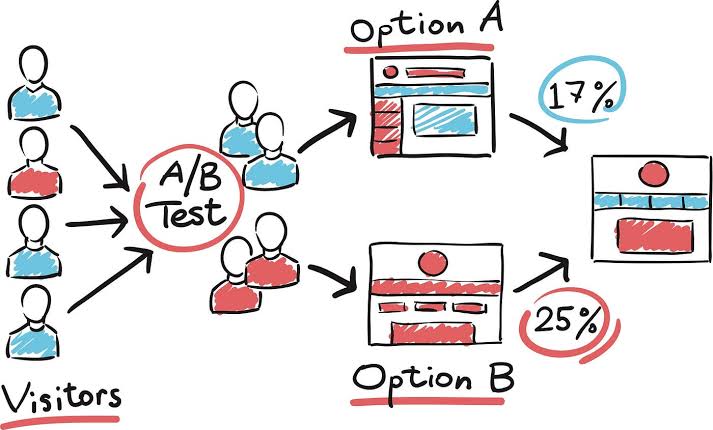
The Importance of A/B Testing in Digital Marketing? A/B testing is a key method in digital marketing that helps businesses make data-driven decisions to optimize their campaigns. It involves comparing two versions of a marketing element (like an ema
See MoreMohamed Asarudeen
Content Marketing Sp... • 5m
Building a Team Collaboration App? Start With Secure Enterprise Chat Software The future of workplace communication is real-time and reliable. If you're building an enterprise chat app, integrating a secure instant messaging API isn't just a featur
See MoreSheikh Ayan
Founder of VistaSec:... • 1y
IoT Hacking Hardware Devices – Understanding Security Risks IoT devices are everywhere—from smart homes to industrial automation. But how secure are they? IoT hacking hardware plays a crucial role in security research, penetration testing, and ethic
See MoreHemant Prajapati
•
Techsaga Corporations • 1y
Bookmark 📑 kar lena dekhte rehna baad:---- . Checklist for First Time Entrepreneur . . 🔍 Validate Your Idea - Conduct customer interviews and MVP testing 📝 Craft Your Business Plan - Define goals, competitive advantages, and finances 🏢 File fo
See More
Download the medial app to read full posts, comements and news.











/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)





















