Back
Sheikh Ayan
Founder of VistaSec:... • 11m
🔍 Top Penetration Testing Post-Exploitation Tools You Should Know! 🚀 Post-exploitation is a crucial phase in ethical hacking, allowing security professionals to maintain access, escalate privileges, and gather intelligence. Here are some powerful tools used in this stage: 🔹 Metasploit – Automates post-exploitation tasks like privilege escalation and persistence. 🔹 Empire – A PowerShell-based framework for post-exploitation and lateral movement. 🔹 Cobalt Strike – Advanced tool for red team operations, including beaconing and pivoting. 🔹 Mimikatz – Extracts credentials and performs pass-the-hash attacks. 🔹 BloodHound – Visualizes and exploits Active Directory relationships. 🔹 PowerSploit – A collection of PowerShell scripts for privilege escalation and reconnaissance. 🛡️ Ethical hackers and cybersecurity professionals, which tool is your favorite? Comment below! ⬇️
More like this
Recommendations from Medial
Sheikh Ayan
Founder of VistaSec:... • 12m
🔥 Top Exploitation Tools for Penetration Testing 🔥 🔹 Metasploit Framework – The go-to tool for developing, testing, and executing exploits efficiently. 🔹 Cobalt Strike – Advanced red teaming tool for post-exploitation, persistence, and lateral
See MoreSheikh Ayan
Founder of VistaSec:... • 1y
Top Metasploit Alternative Tools for Penetration Testing Metasploit is a powerful penetration testing tool, but several alternatives offer robust features for ethical hackers and security professionals: 1. Nmap – A fast network scanner for discover
See MoreSandeep Jangir
Cyber Security Profe... • 6m
🚨 Calling all Cybersecurity Trainers! 🛡️ I’m looking to connect with skilled and passionate Cybersecurity Trainers for an exciting opportunity. If you're experienced in delivering hands-on training in areas like: 🔹 Ethical Hacking 🔹 Network Sec
See MoreSheikh Ayan
Founder of VistaSec:... • 1y
IoT Hacking Hardware Devices – Understanding Security Risks IoT devices are everywhere—from smart homes to industrial automation. But how secure are they? IoT hacking hardware plays a crucial role in security research, penetration testing, and ethic
See MoreSheikh Ayan
Founder of VistaSec:... • 11m
🚀 How to Do Firm Branding Using Social Media 💡 Social media is a powerful tool to build trust, engagement, and authority. 🔹 Define Your Brand Voice – Is your brand professional, playful, or inspirational? Keep it consistent across all platforms.
See MoreVIJAY PANJWANI
Learning is a key to... • 2m
Cash-Rich Indian Companies – Power of Strong Balance Sheets! 🇮🇳📊 Ever wondered which Indian companies are sitting on massive cash reserves? These cash-rich giants have strong financial stability, resilience during downturns, and the power to inv
See More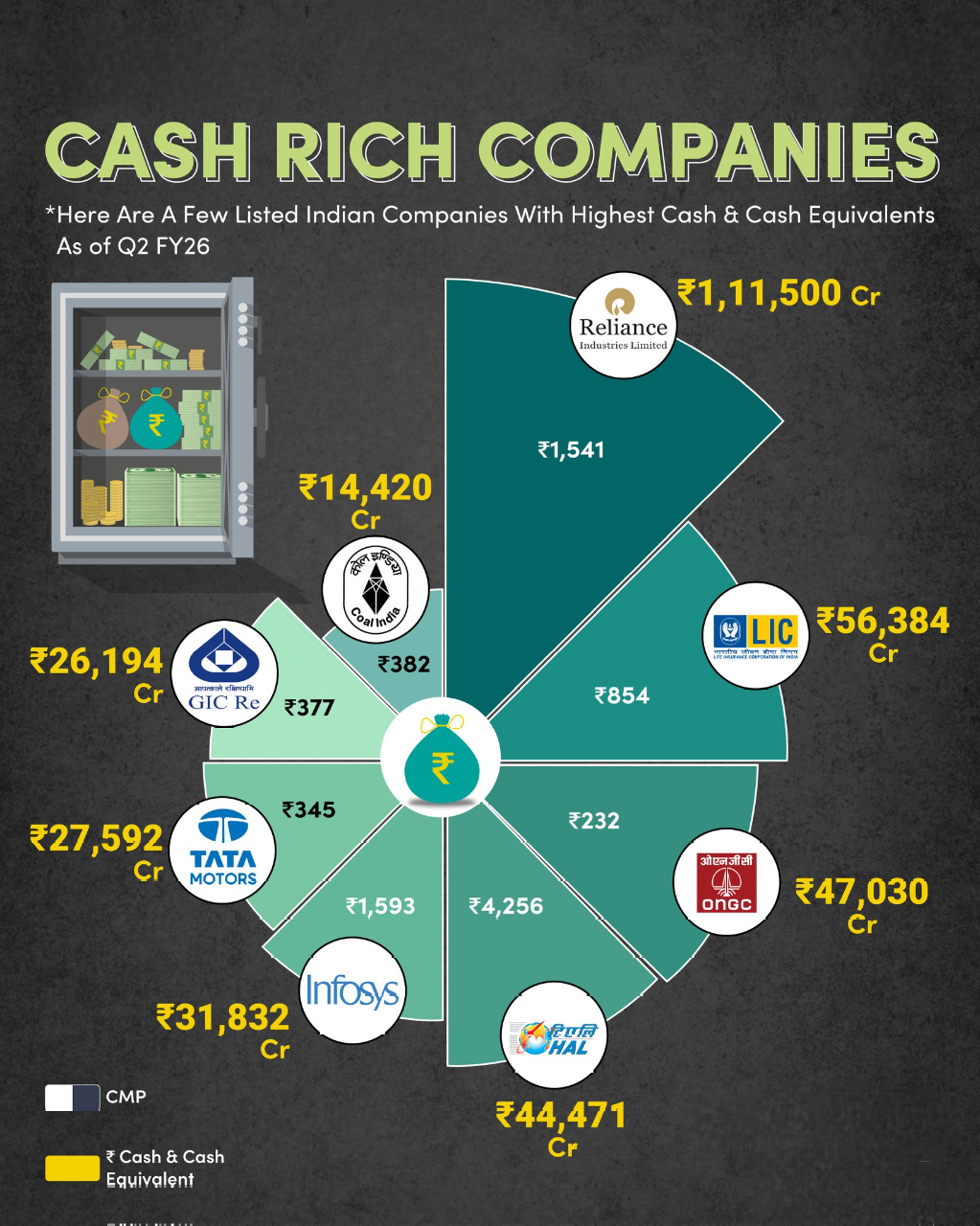
Abhishek Kumar
Co-founder and COO • 5m
Excited to share about JeevanX AI! 🚀 I’m Abhishek Kumar Maurya — Co-Founder & COO of KwikMedi and Founder of JeevanX, the world’s first AI avatar-powered wellness & farming platform. We’re building a system where AI doctors, therapists, fitness co
See MoreJatin Ahirwar
Full Stack Developer • 1y
📊 Day 29 of the 30-day Question Mania challenge with Hitesh Choudhary Sir! 📊 Today, I worked on creating a Social Media Dashboard, bringing together several key elements to create an interactive and user-friendly platform. Here’s what I accomplish
See MoreDownload the medial app to read full posts, comements and news.








/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)





















