Back
Sheikh Ayan
Founder of VistaSec:... • 11m
🔍 Top Programming Languages & Tools for Exploit Development & Reverse Engineering 🛠️ 🚀 Top Programming Languages 🔹 C & C++ – Low-level access, memory manipulation 🔹 Assembly (x86, x64, ARM) – Essential for understanding binaries 🔹 Python – Scripting for automation and exploit development 🔹 Rust – Secure memory management, modern alternative to C/C++ 🔹 JavaScript – Useful for browser-based exploitation 🛠 Essential Tools 🔸 Ghidra & IDA Pro – Advanced disassemblers for binary analysis 🔸 Radare2 & Binary Ninja – Lightweight reverse engineering tools 🔸 OllyDbg & x64dbg – Dynamic debugging for Windows binaries 🔸 Metasploit – Powerful framework for exploit development 🔸 Pwntools – Python library for CTFs & exploit scripting 🔸 Frida & Hopper – Dynamic instrumentation & mobile RE 🔸 Immunity Debugger – Exploit writing & vulnerability analysis
More like this
Recommendations from Medial
Shivam Dubey
Data Alchemist | Py... • 1y
Remove Leaf Nodes with Target Value in a Binary Tree | C++ Tutorial 🔗 **Watch Now:** [Remove Leaf Nodes with Target Value in a Binary Tree | C++ Tutorial]. ✨ Don't forget to like, share, and subscribe for more coding tutorials! 📢 **Tags:** #Bina
See MorePRADEEP BIJARNIYA
Founder & COO @Oogle... • 8m
🚀 Building a Tech or AI Product? Let Ooglesoft handle it for you! 🔹 Web & App Development 🔹 Custom AI Tools & Automation 🔹 Viral Branding & Launch Strategy Got an idea? Just DM us — we turn visions into working products. 📩 Message us now to get
See MoreVENTURE NAVIGATOR
INVESTOR | Start up ... • 1y
Why One Startup Got Funded & The Other Didn’t? 🚀💰 Recently, I validated two pitch decks. One secured funding, while the other is still seeking investors. The difference? Smart financial planning vs. unnecessary burn. ✅ Funded Startup: 🔹 Allocat
See MoreThakur Ambuj Singh
Entrepreneur & Creat... • 10m
Startup Funding Guide: From Idea to Growth 🔹 Pre-Seed – Building a concept & team 🔹 Seed – Validating market fit 🔹 Series A – Scaling revenue & profitability 🔹 Series B – Expanding market share 🔹 Series C & Beyond – Preparing for IPO & market l
See More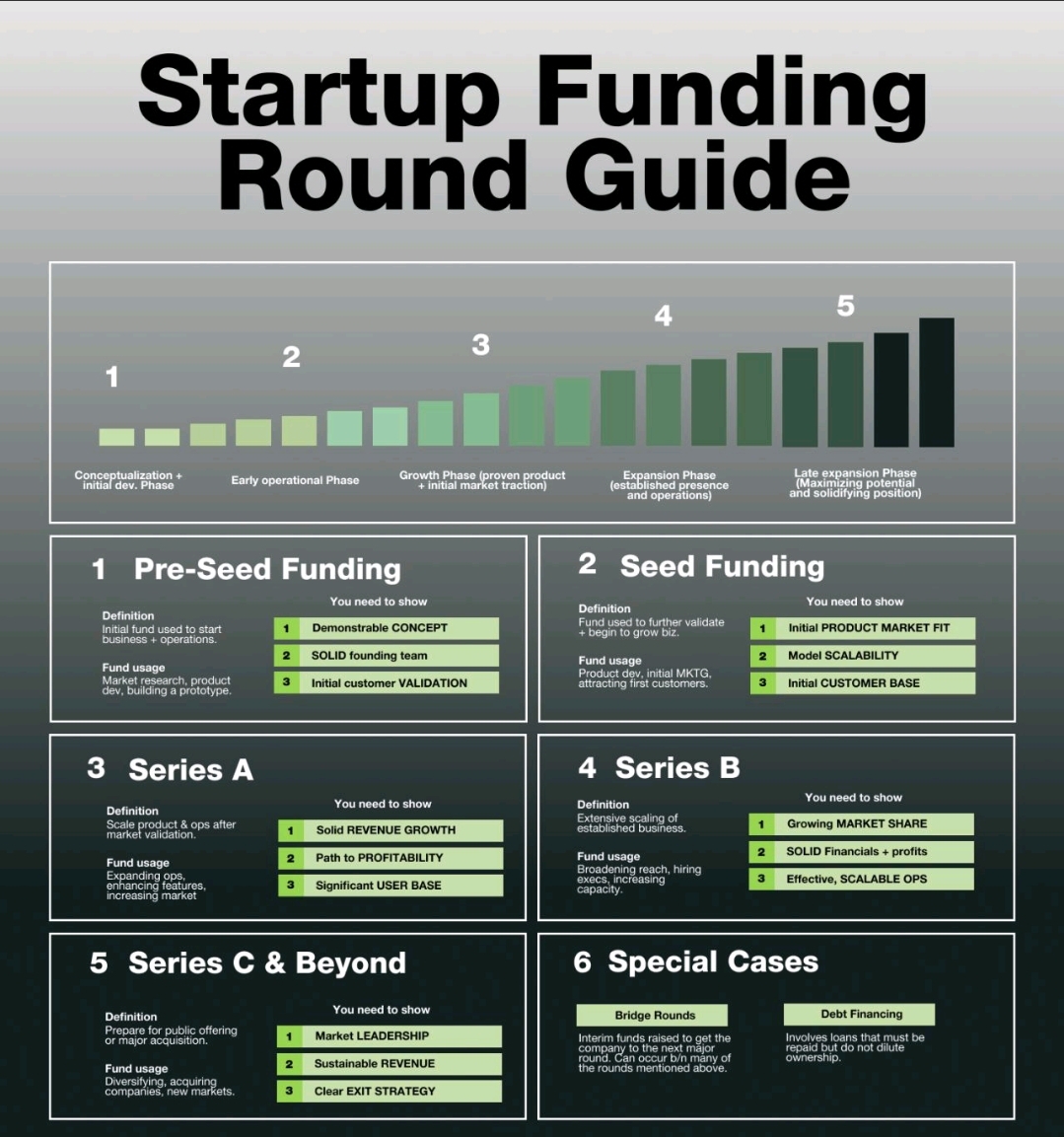
Jinal Chauhan
Helping businesses g... • 7m
Looking to bring your idea to life? We help startups build powerful websites and mobile apps that are fast, scalable, and launch-ready. 🔹 Website Development 🔹 Android & iOS App Development 🔹 CRM & Custom Tools 💡 Whether you're at Day 1 or sca
See MoreDownload the medial app to read full posts, comements and news.












/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)





















