Back
Afifa
"I am the architect ... • 1y
It is critical for everyone, not just professionals in the field—to be informed and vigilant about digital security. But are we asking the right questions? I’ve been thinking a lot about how much we know about staying safe online. Are we asking the right questions? Do we get the risks we face every day, or are we just hoping someone else will take care of it? Cyber threats are real, and they’re not going anywhere. Let’s talk about it, what is your biggest worry when it comes to cybersecurity?

Replies (6)
More like this
Recommendations from Medial
Sairaj Kadam
Student & Financial ... • 11m
Selling isn’t about being clever. It’s not about throwing mud at the wall and hoping it sticks. It’s about asking the right questions, planting the right seed, and letting it grow. The best salespeople don’t pitch. They help people realize what the
See MoreVasvi Seth
Cyber Security Stude... • 1y
🔒 As an entry-level security analyst, safeguarding organizational assets against threats is paramount. Understanding the various forms of threats is key to fortifying our defenses. Here are two common types every analyst should be vigilant about: •
See MoreDivyam Gupta
Building products, l... • 9m
I was contacted by someone from Medial about a business idea and on asking more questions about the business, this was their response. I have met so many people who are crore pati or have done well in their life but never faced something like this.
See More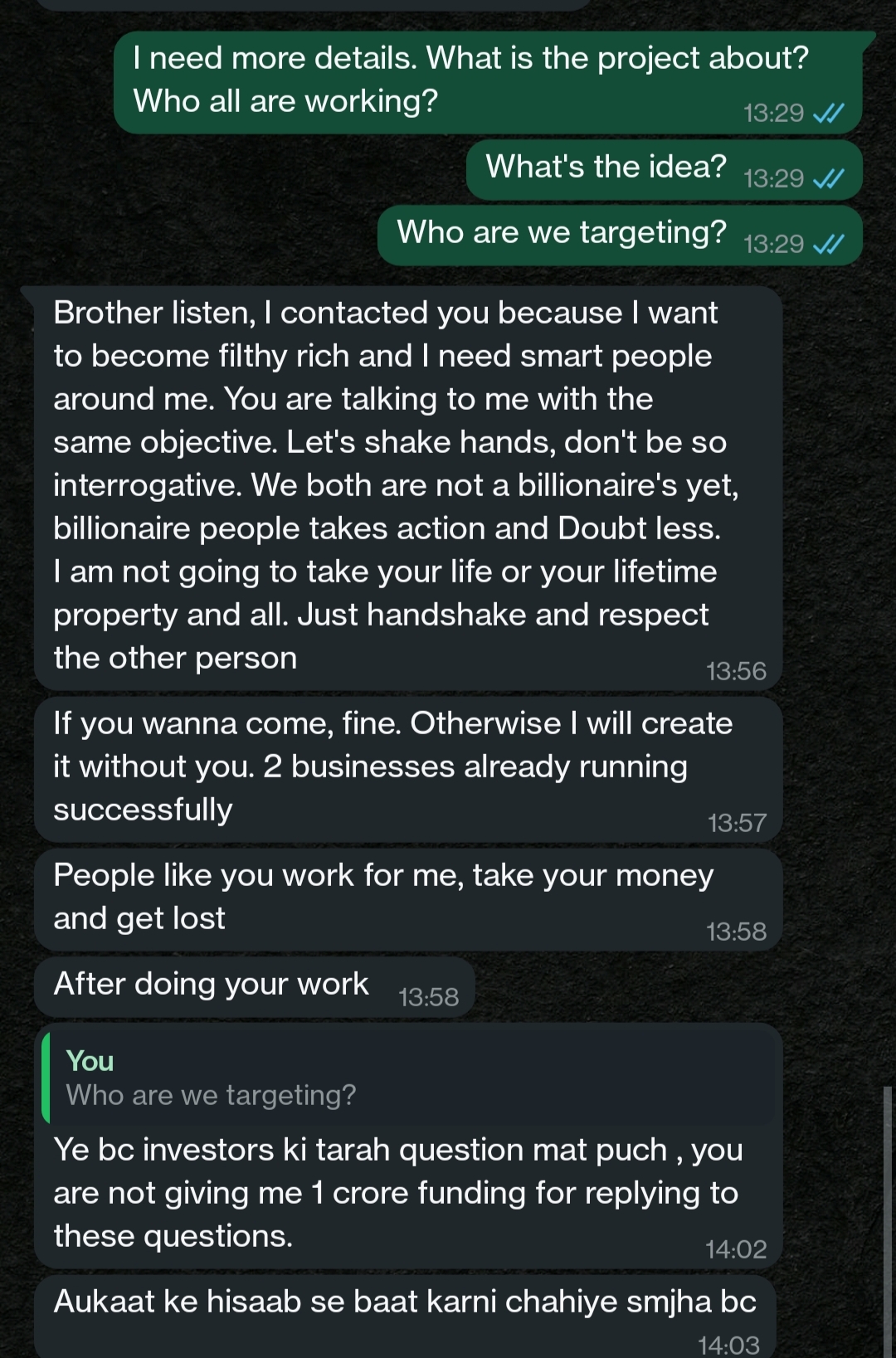
Download the medial app to read full posts, comements and news.
















/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)





















