Back
Replies (1)
More like this
Recommendations from Medial
Vasvi Seth
Cyber Security Stude... • 1y
Protecting personal data is crucial in today's digital landscape. Personally Identifiable Information (PII) encompasses any data that can be used to discern an individual's identity. Safeguarding PII is not just a responsibility; it's a commitment to
See MorePranab Kumar Sahoo
Hey I am on Medial • 1y
From the recent interaction, I think Medial is something like twitter but without any noise, politeness, more interaction between users for getting to know each other, some cool features (mostly anonymous) & a pretty cool UI man!! I'm loving it...🤩
See MoreSaket Sambhav
•
ADJUVA LEGAL® • 7m
Have you heard about the Otipy mess? The popular grocery app just shut down out of nowhere - people can’t get their money back, employees aren’t getting paid, and the founders have totally disappeared! Now everyone’s asking for an official investi
See MoreAniruddha V
17 year old Founder • 7m
Not really into sharing stories but here it's probably gonna reach right people October 2024 I dropped out from high school I'm an entrepreneur I'm working on a app As well as a personal brand I work every single day I workout 6 times a week Get prop
See MoreVasvi Seth
Cyber Security Stude... • 1y
🔒 As an entry-level security analyst, safeguarding organizational assets against threats is paramount. Understanding the various forms of threats is key to fortifying our defenses. Here are two common types every analyst should be vigilant about: •
See MoreGautam Pareek
याचना नहीं अब रण होग... • 1y
Few hours ago I open my friends chat and instagram shows me a pop up notification (Sorry I forgot to take SS) that is"is this chat related to your business goals?" I amazed to see this notication ..insta Really going to be extreme personal soon....
See MoreDownload the medial app to read full posts, comements and news.







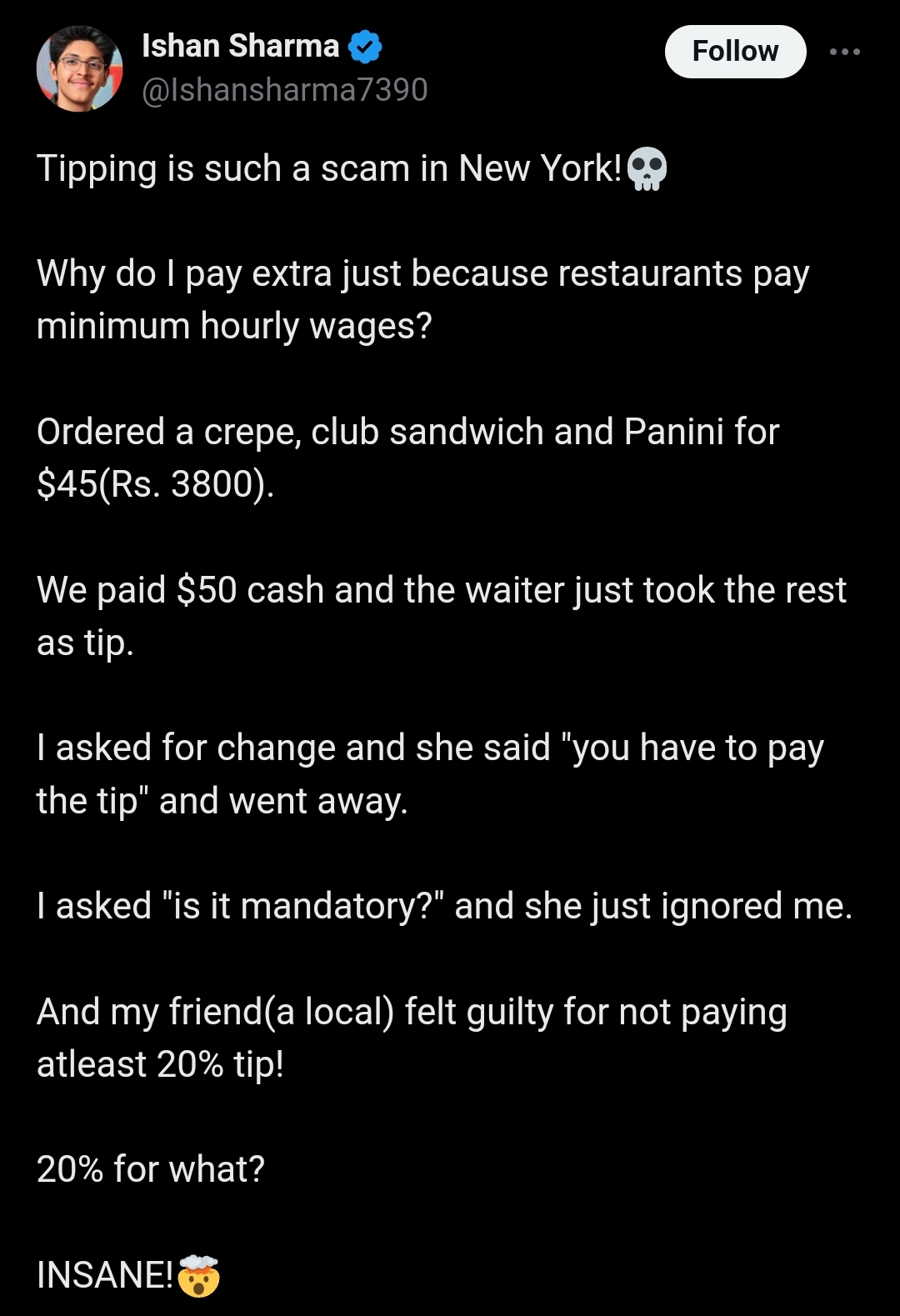







/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)


















