Back
Shrijeet
Expect me!! • 7m
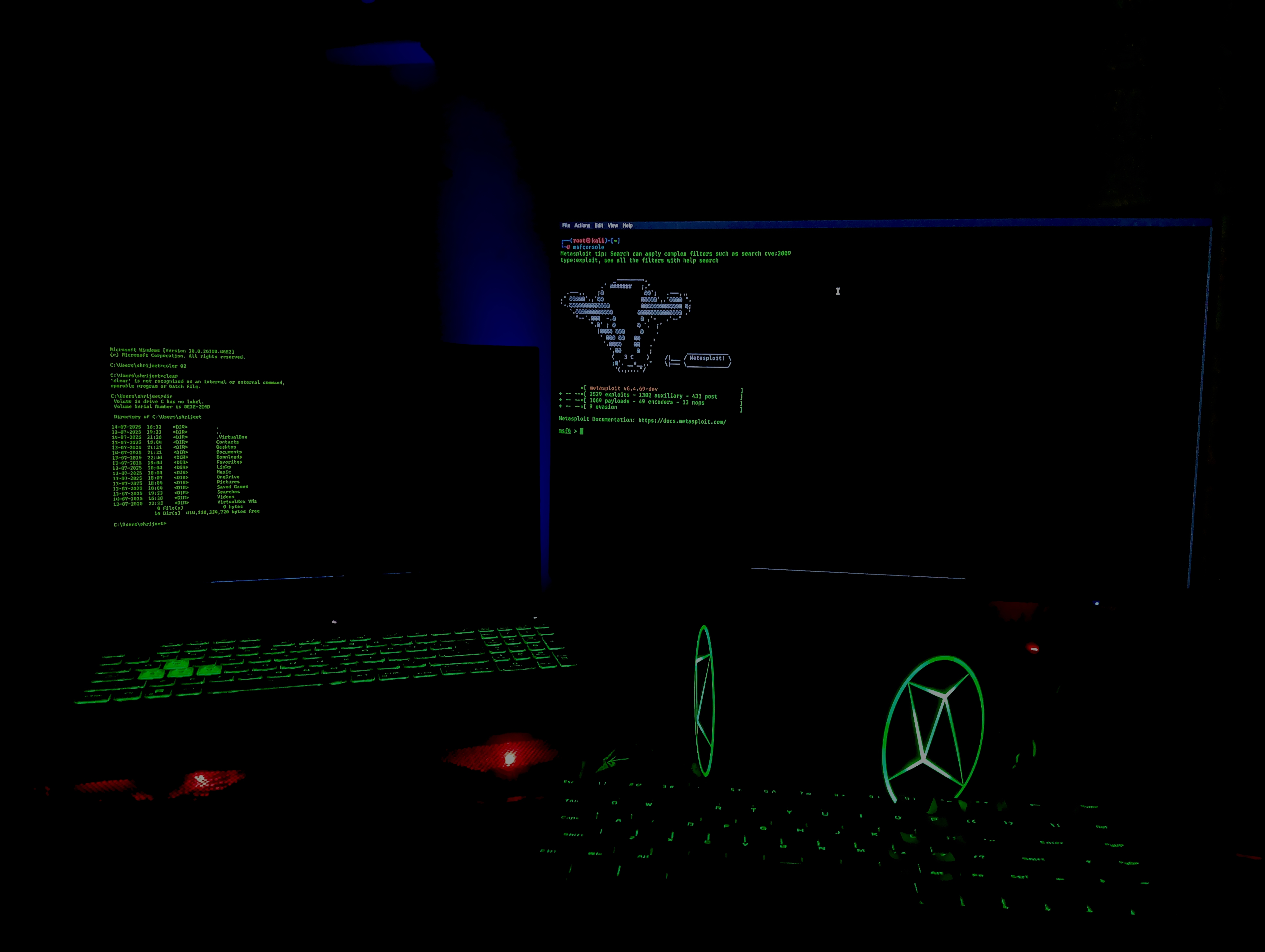
This isn't just a computer, it's a launchpad for thousands of payloads and exploits. Welcome to the mind of a 17y/o hacker #hacking
Replies (11)
More like this
Recommendations from Medial
Sheikh Ayan
Founder of VistaSec:... • 7m
🔴 Red Teaming Tips & Tricks Red Teaming isn't just about hacking — it's about thinking like a threat actor and testing an organization’s detection, defense, and response capabilities. 🛠 1. Blend In with Normal Traffic Use tools like Cobalt Strike
See MoreRitesh gautam
Cyber Security Enthu... • 1y
Excited to kickstart my career in tech! With a degree in Computer Science and a diploma in Cybersecurity & Ethical Hacking, I'm eager to contribute my skills. Open to entry level opportunities in #Cybersecurity, #EthicalHacking, and more tech field.
See MoreEddie Jolley
Hey I am on Medial • 1m
Best Crypto Bitcoin Recovery Service | Best Crypto Asset Recovery Service Hire iFORCE HACKER RECOVERY I spent a lot of time researching ways to recover stolen Bitcoin after I unexpectedly lost $120,000 during a trade. During my search, I came across
See More
Sheikh Ayan
Founder of VistaSec:... • 1y
Boost Your Penetration Testing with These Top Burp Suite Extensions! Supercharge your security assessments with Burp Suite’s powerful extensions. Here are the top picks every ethical hacker needs: 1. JSON Beauty: Simplify and beautify complex JSON
See MoreDownload the medial app to read full posts, comements and news.














/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)




















