Back
Nandha Reddy
Cyber Security | Blo... • 8m
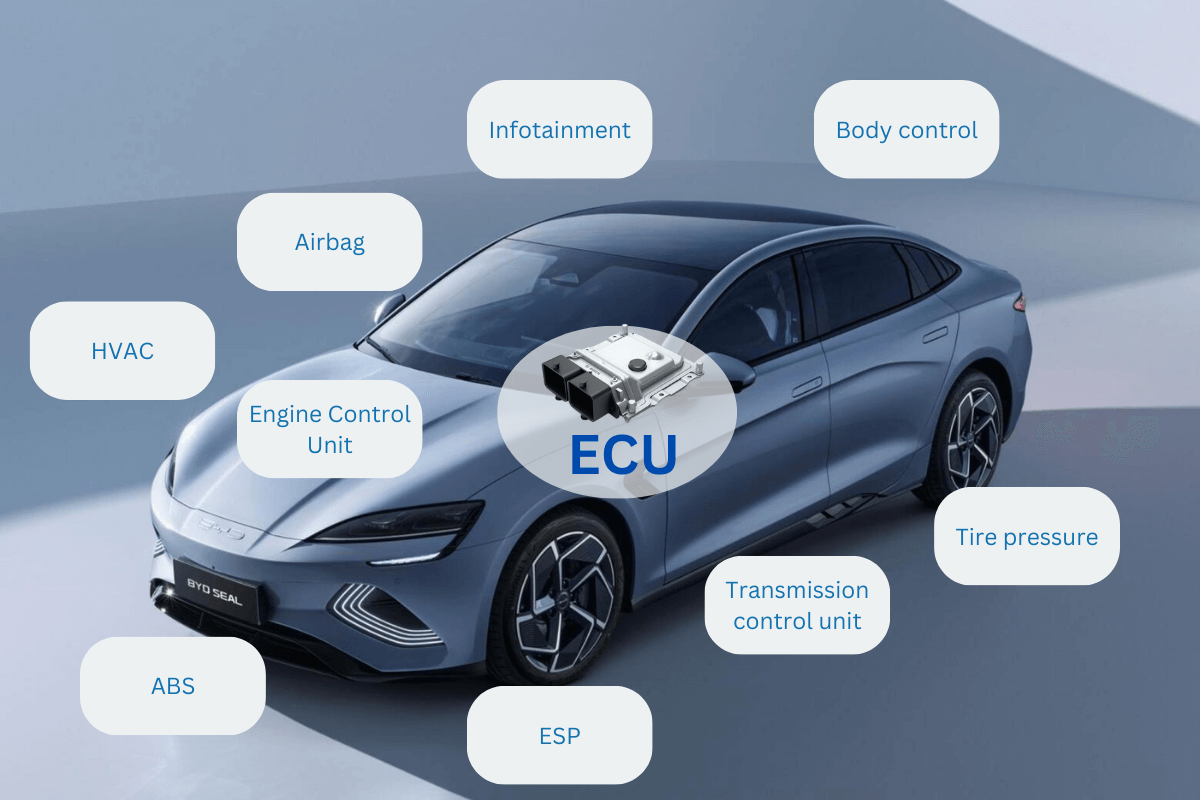
POST :1 (SECURITY) Securing the Brains of Modern Cars: My Deep Dive into Automotive ECUs 🚘🧠 This week, I took a leap into how modern vehicles are not just mechanical machines, but intelligent systems powered by ECUs (Electronic Control Units) — and how security is becoming a first-class citizen in the automobile industry. As a cybersecurity learner, this opened up a whole new dimension for me. Here’s a brief look at what I explored: 🛡 1. CSMS (Cyber Security Management System) The ISO/SAE 21434 standard ensures security is considered from design to disposal. Think: secure boot, access control, and encrypted firmware updates. 📌 Example: If firmware is tampered, a car might refuse to start and notify the cloud — thanks to CSMS enforcement! 🔐 2. HSM (Hardware Security Module) This is a tamper-proof crypto co-processor inside the ECU. It secures keys, signs messages, and prevents key theft even during physical attacks. 📌 Used for secure boot, MAC (message auth code) generation, and secure CAN communication. 🧠 3. Linux Device Drivers in ECUs Drivers act as a bridge between hardware and the OS kernel. Each hardware component (IMU, GPS, etc.) needs a dedicated driver for real-time performance and fault tolerance. 📌 Example: IMU sensors use the I2C protocol and rely on kernel-level drivers. 🌐 4. Ethernet Switches in Automotive These manage high-speed, time-sensitive traffic between ECUs. Essential for domains like ADAS, infotainment, and cameras. 📌 Example: 4 cameras connected to ECU via TSN Ethernet ensures collision-free data flow. 🧪 5. Virtual ECU Testing Systems Used to simulate and test ECU behavior without real hardware. Frameworks like CANoe and MATLAB help catch bugs early in development. 📌 Also great for testing over Docker and simulating real-time faults. 🔏 6. Cryptographic Device Driver Development These drivers help OS-level software talk to crypto hardware. 📌 Example: During car boot, firmware is verified using ECC. If verification fails, the vehicle halts — critical for safety! ✨ Why this matters for Cybersecurity students like me? Because automotive is the new frontier for hacking and protection. As we move toward autonomous and connected vehicles, understanding how ECUs work and how to secure them is a superpower. Let's keep learning and driving forward 🚀 #Cybersecurity #AutomotiveSecurity #ECU #EmbeddedSystems #HSM #ISO21434 #CANBus #LinuxDrivers #AutomotiveNetworking #VehicleSecurity #LearningJourney #LinkedInLearning



Replies (5)
More like this
Recommendations from Medial
Bharat Gautam
Build something that... • 8m
Open for Partnership 😉 Let's build something that can chenge everything Looking for Collaborators: Building a Universal ECU Tuning Tool for Phones & Laptops 🔧💡 Hey folks! I’m working on an ambitious project and looking for developers, automotiv
See MoreNishal S K
Tech-Powered, Future... • 4m
Hey everyone 👋 I’m open to collaborating with startups, teams, or individuals who are working on exciting ideas in embedded systems, automotive technology, or hardware innovation. I specialize in hardware–software integration, embedded development
See MoreVasvi Seth
Cyber Security Stude... • 1y
🖥️ Understanding Computer Booting: BIOS vs. UEFI When you power on your computer, it's more than just pressing a button. The process involves two essential microchips: BIOS (Basic Input/Output System) and UEFI (Unified Extensible Firmware Interface
See MoreMayur Chavan
Turning innovation i... • 1y
🚀 Hey fellow innovators! Let's talk about my game-changing IoT platform designed to shake up the tech world! Here's what makes it stand out: Opportunity for you: core team /build product with us Versatility: With support for all available microproc
See MoreAnkan Bayen AV
Founder & CEO of Bab... • 1y
📌what is Babe AI ? ✅Babe AI, developed by Babe Finance, revolutionizes digital finance with cutting-edge security, AI-driven insights, and seamless crypto transactions. It empowers users with smarter, safer financial solutions. 📌 website releas
See More
Pratik Bhavarthe
Full Stack Engineer ... • 8m
🚨 We’re Hiring: Embedded Firmware Engineer | Pluto (On-site, Gurgaon) We’re building an EV platform from the ground up—and we need a firmware engineer who can do the same. At Pluto Mobility, you’ll design and develop real-time firmware for BMS, VC
See More
Download the medial app to read full posts, comements and news.












/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)





















