Back
Shubham
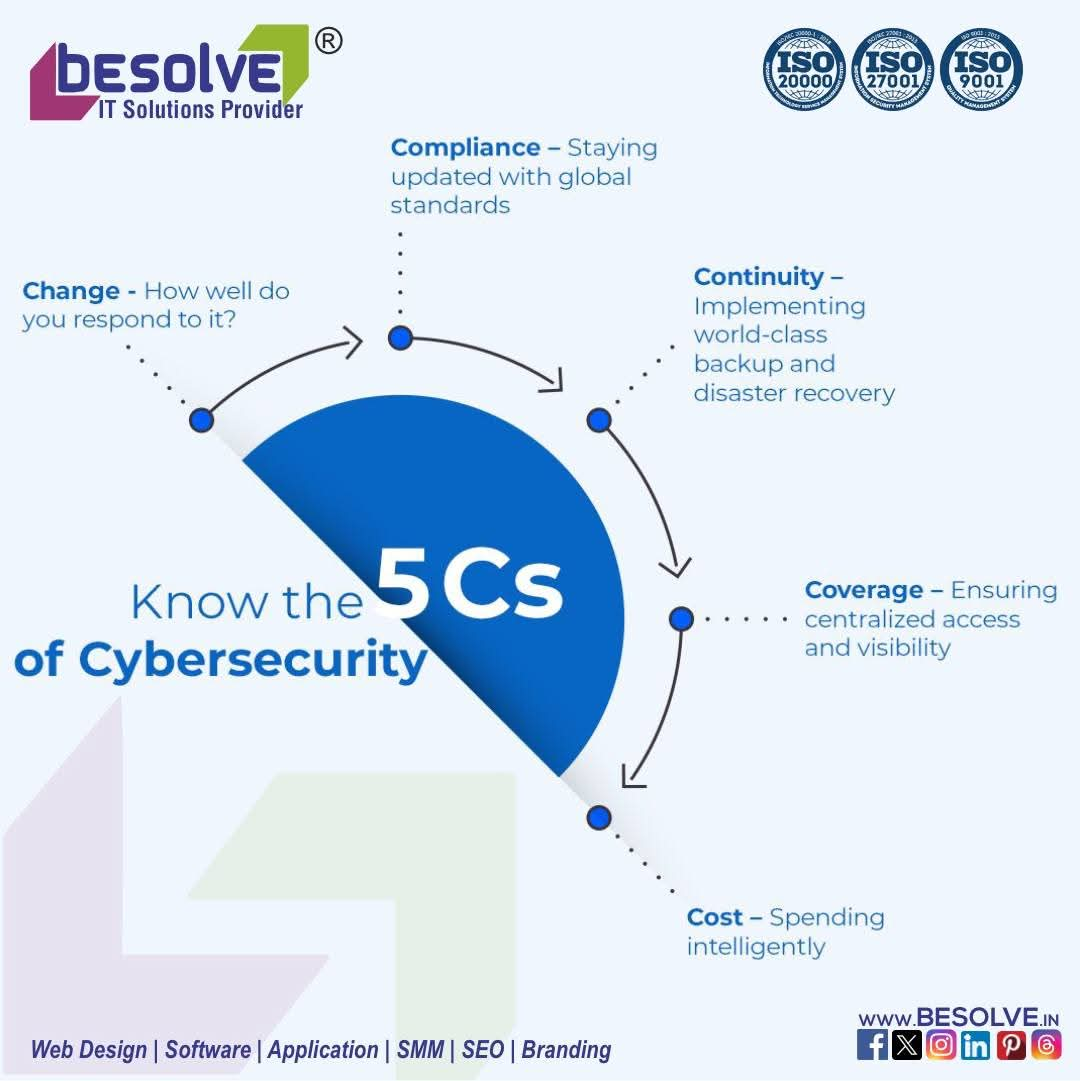
"Exploring Cybersecu... • 1y
Why Are Some Startups Ignoring Security? As a web penetration tester, I’ve reported many bugs to startup websites, including serious ones that put user data at risk. Yet, some of these issues are never fixed. Startups often focus on growth and new features, but ignoring security can lead to data breaches and loss of trust. Fixing vulnerabilities early is cheaper and safer than dealing with a breach later. Startups must start taking security seriously—it's not optional, it's a responsibility.
More like this
Recommendations from Medial
Saranyo Deyasi
I am the exploit • 4m
Currently researching the security domain of AI ethics, exploring how vulnerabilities in AI models can lead to data breaches and adversarial attacks. My focus is on building secure, transparent AI systems that defend against manipulation. #AIEthics #
See MoreBusiness Digital Twenty Four
Innovation | Insight... • 9m
TikTok Fined €600 Million for Data Breaches: What It Means for EU Users and Global Tech. European Regulators Crack Down on TikTok Over Data Transfers to China and GDPR Transparency Failures https://bdigit24.com/tiktok-fined-600-million-euros-for-ill
See MoreDataSpace Academy
Learn, Secure & Earn • 10m
What are the Top 3 Data Analytics Security Threats? Rising incidents of data breaches have put a big question mark on data safety. Added to these, there is the issue of poor Data quality and more. The blog here highlights major data analytics securi
See More
Download the medial app to read full posts, comements and news.







/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)





















