Back
Comet
#freelancer • 1y
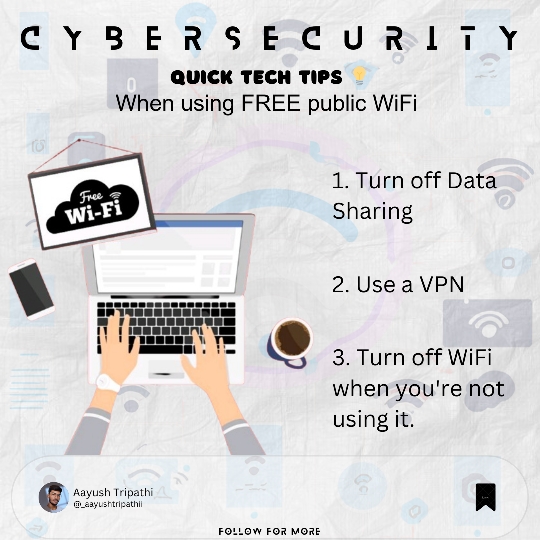
🔒 Ready to boost your online safety? Here are 15 essential cybersecurity tips for 2024 that everyone should know! From strong passwords to using VPNs, let's secure our digital lives together. Which tip do you think is a must? Share your thoughts!
Replies (2)
More like this
Recommendations from Medial
Vasvi Seth
Cyber Security Stude... • 1y
🔒 Cybersecurity, also known as security, is paramount in today's digital age. It's the practice of safeguarding the confidentiality, integrity, and availability of information by fortifying networks, devices, and data against unauthorized access o
See MoreBansidhar Tigga
Transform your compa... • 8m
🚀 Stay ahead in the #eCommerce game! Discover the latest trends, expert tips, and marketing insights on our blog. Learn how to: * Master budgeting for maximum ROI 💰 * Turn social media likes into sales 📈 * Boost cybersecurity for your platform
See MoreAccount Deleted
Hey I am on Medial • 1y
🚨 Security Alert: The GodLoader malware has exploited vulnerabilities in the Godot Game Engine, compromising over 17,000 systems in just three months. This incident highlights the urgent need for robust cybersecurity measures within the gaming commu
See More
Vasvi Seth
Cyber Security Stude... • 1y
🔒 Principle of Least Privilege: Enhancing Security and Efficiency🔒 In cybersecurity, the Principle of Least Privilege (PoLP) is paramount. It means granting users only the minimal access necessary to perform their tasks. By limiting permissions, w
See MoreSheikh Ayan
Founder of VistaSec:... • 11m
🔒 How to Secure Your System & Servers Like a Pro! 🚀 Follow these advanced tips to safeguard your systems and servers from potential attacks: ✅ Enable Multi-Factor Authentication (MFA) – Add an extra layer of security beyond passwords. 🛡 Implemen
See MoreDownload the medial app to read full posts, comements and news.













/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)




















