Back
Saksham
Legal Advisor! • 1y
Hi Aaditya, since you are still in the development stages, I'd request you to work on the revenue system by keeping the following points in mind: 1. You'd require to specifically disclose what data are you storing and why are you storing before taking consent from the users for their data. 2. Any user can request you for deletion of their data and you'd need to strictly comply with the same. 3. Only the necessary data can be stored on the servers. 4. Highest level of cybersecurity procedures. Each data breach can lead to fines of up to Rs 250 Crores. If you have any doubts or anything, I'm happy to help.
Replies (1)
More like this
Recommendations from Medial
Vishnu Teja
Vedh's India Pvt Ltd • 7m
When I'm trying to make payment or register for a website or address field the details are automatically filled That means my data is leaked. I believe Cred leaked my personal data as the Cred UPI shows there. Please share your thoughts for account
See MoreSudarshan Pal
Data Engineer @Quant... • 1y
Many argue that Data Engineering is a part of data science and analytics. It's different from data science, but they work together closely. Data Engineers come first in the process. They gather and organize data. This data is then used by Data Scien
See More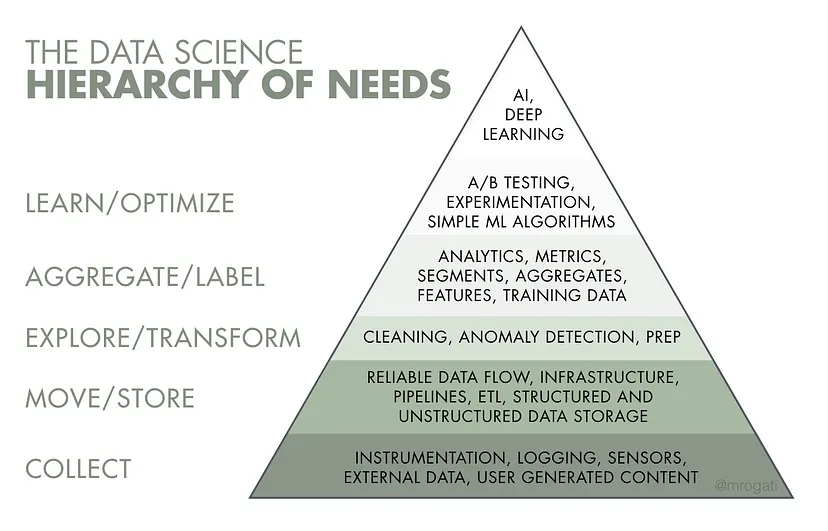
Prince Yadav
Co -founder at Trade... • 1y
Prefix data structure, often referred to as a trie, is a tree-like data structure used for storing and retrieving a dynamic set of strings efficiently, particularly when dealing with prefix-based operations. #Datastructure #codingjourney Prefix Expr
See More
Download the medial app to read full posts, comements and news.






































/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)



















