Back
Shiva Prasad
•
Lognormal • 8m
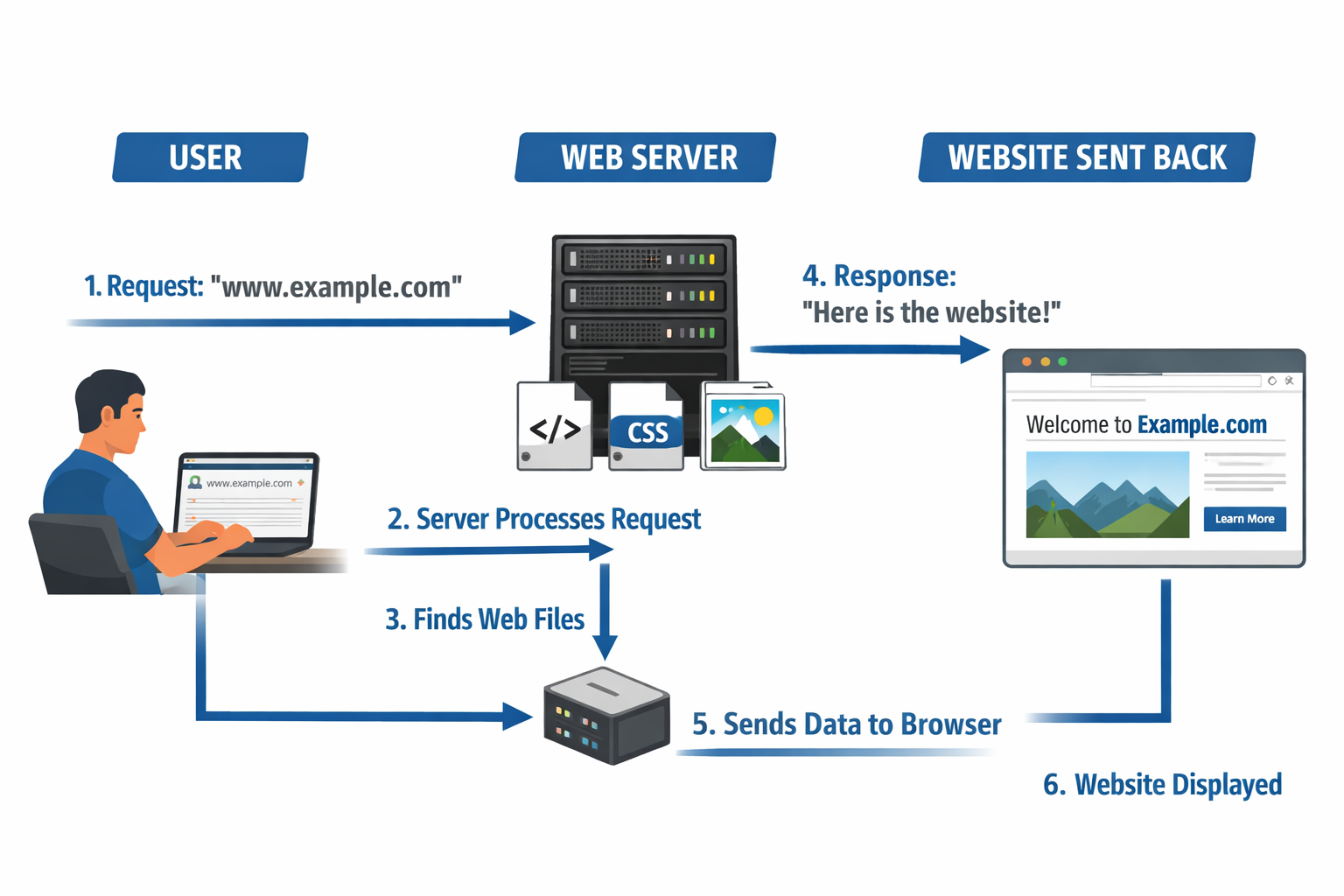
I suggest using DNS Provider like cloudflare and then. use A record to point to your web server. It protects from Server IP Publishing and DDOS Attack with free SSL and more
More like this
Recommendations from Medial
Abdul Alim
Building Lovable for... • 3m
Crazzy Grind Day 23 ⚡ Today’s plan was simple — spend the whole day on SEO and marketing. But then someone told me, “Hey, Crazzy’s server isn’t working.” I checked everything — backend, frontend, domain, even logs. After hours of digging, I finally
See MorePAVANKALYANNAIK A
Co founder at Scuts • 1y
Hello Our app is developed in Flutter and node js. We have out sourced people to develop it. We have deployed our app on E2E networks server. When we are publishing our app into playstore. Playstore rejected app for reasons: • Internal server error
See MoreArnav Aggarwal
Love to Code | React... • 10m
Hit an unexpected 'rate limit' message while creating Studio Ghibli-style images on ChatGPT? You weren't alone.This is a great example of API traffic management techniques like Rate Limiting and Throttling. ➡️Rate Limiting - Sets a hard cap; reque
See More
Vasvi Seth
Cyber Security Stude... • 1y
Understanding Network Protocols: The Backbone of Digital Communication In the world of networking, protocols are crucial. A network protocol is essentially a set of rules used by two or more devices on a network to dictate the delivery and structure
See MoreVasvi Seth
Cyber Security Stude... • 1y
Exploring Communication Protocols: Transmission Control Protocol (TCP) Communication protocols are the cornerstone of network transmission, dictating how data is exchanged between devices. They ensure efficient and reliable communication, including
See MoreSheikh Ayan
Founder of VistaSec:... • 11m
🚨 Critical Alert: Ransomware Attack on Ardent Health Services 🚨 In November 2023, Ardent Health Services fell victim to a ransomware attack, forcing the healthcare provider to take its network offline to contain the damage. This led to operational
See MoreDownload the medial app to read full posts, comements and news.














/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)





















