Back
Replies (1)
More like this
Recommendations from Medial
Darsh Singh
Ask me no questions ... • 1y
Decentralized Social Media on IPFS IPFS provides a decentralized and immutable approach to data storage, much like how blockchain technology decentralizes transactions. Imagine a DeFi platform offering tokenized real estate. By storing property docum
See More
Anonymous
Hey I am on Medial • 1y
Idea: immutable journal app Once you write something, it is stored on Blockchain and time stamped in hash format, and it cannot be changed. The written journal is then time capsuled and can be opened after a week, month, or even a year. It also inclu
See Moresujit singh
•
Dual Infotech Group • 1y
A Blockchain-Based Data Security System for Android and iOS devices ensures the highest level of data protection by leveraging blockchain technology. This system allows users to track their mobile data in real-time, providing alerts if any data is st
See MoreVasvi Seth
Cyber Security Stude... • 1y
Protecting personal data is crucial in today's digital landscape. Personally Identifiable Information (PII) encompasses any data that can be used to discern an individual's identity. Safeguarding PII is not just a responsibility; it's a commitment to
See MoreVasvi Seth
Cyber Security Stude... • 1y
💻 Embracing Cloud Security: Ensuring Data Protection in the Digital Realm 🔒 Cloud security is more than just a buzzword; it's a critical process ensuring that assets stored in the cloud are properly configured and access is restricted to authorize
See MoreAnonymous
Hey I am on Medial • 2y
Hello Fellow Medial users !! I have an idea that could completely revolutnalise the overall architecture of data. So here is the idea. Consider 3 android devices, a user named "A" hastko log in to an app. He enters his password. The app communicates
See MoreSanskar
Keen Learner and Exp... • 4m
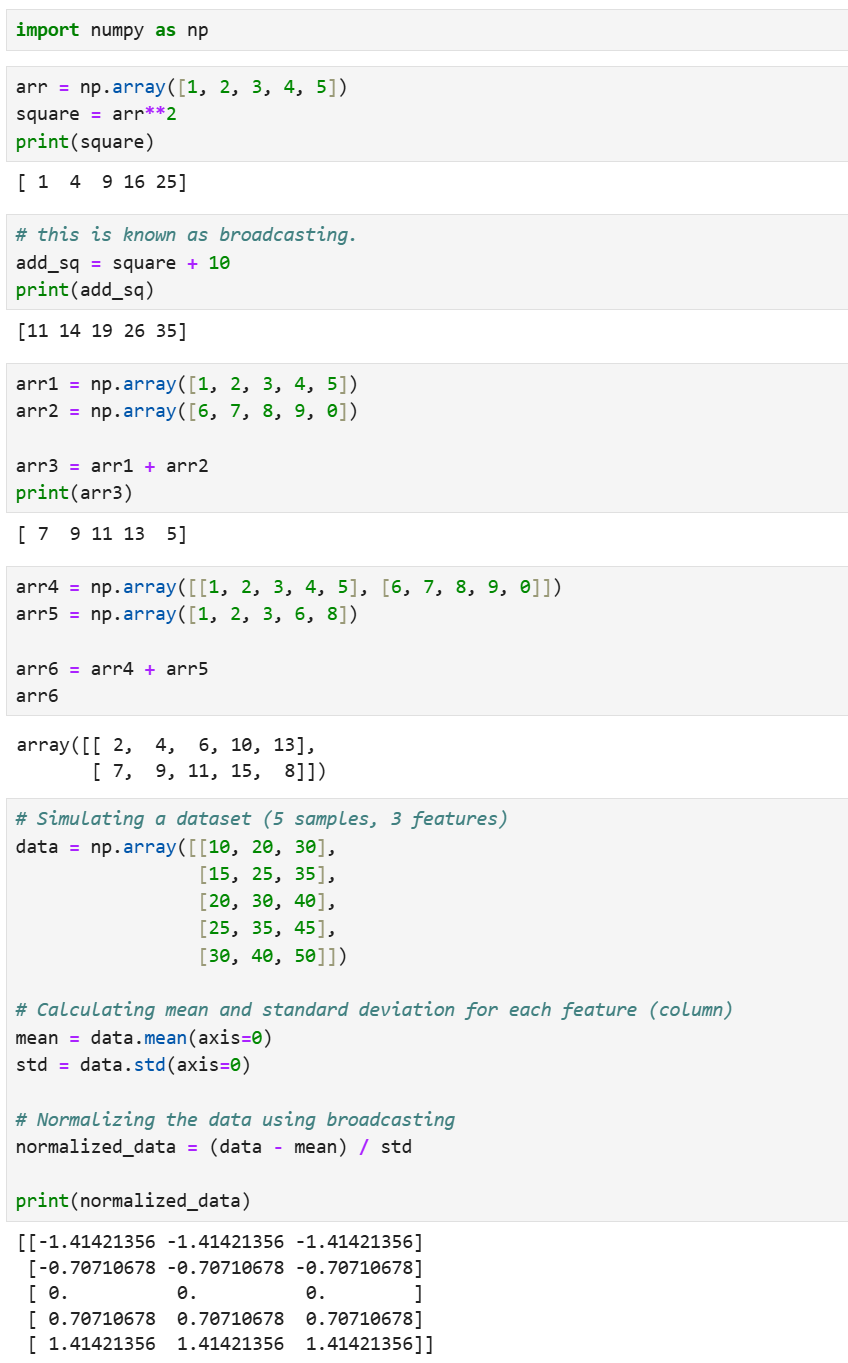
Day 9 of learning Data Science as a beginner. Topic: Data Types & Broadcasting NumPy offers various data types for a variety of things for example if you want to store numerical data it will be stored in int32 or int64 (depending on your system's a
See More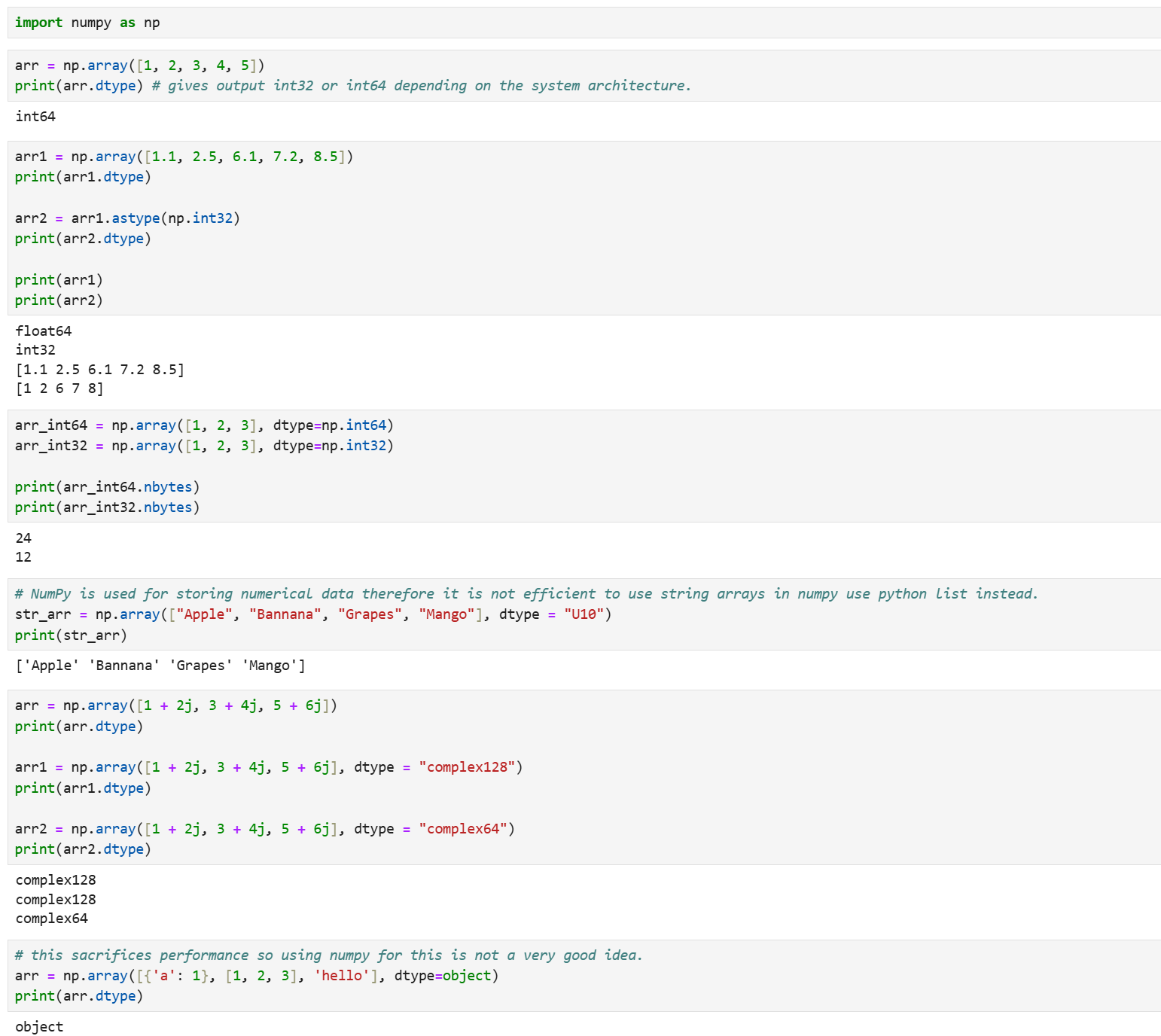
Download the medial app to read full posts, comements and news.

















/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)





















