Back
Replies (1)
More like this
Recommendations from Medial
Tharuneshwar S
Technology Rapt | Py... • 1y
I have an idea to build an virtual-try-on software for apparel. Where you can view your outfit in 360 deg using 3d modeling technology which mimic you. Outfit recommendation engine. It recommends various outfits based on the ocassion. Share your v
See MoreChenab Chavan
Work hard party hard... • 1y
Working on Anime Cosplay Cloth rental Business As People who want to cosplay don't want to buy the clothes as it can't be used on another event. What do you think about this ? Your quick review will be very helpful. The only concern is I am not sure
See MoreJAGDEEP SINGH RANDHAWA
Wait and watch • 1y
Upcycled Fashion Rental Service * Concept: Rent out unique, stylish clothing items made from upcycled materials (e.g., repurposed textiles, vintage clothing). * Unique Twist: * Curated collections: Offer limited-edition collections designed by l
See MoreDownload the medial app to read full posts, comements and news.





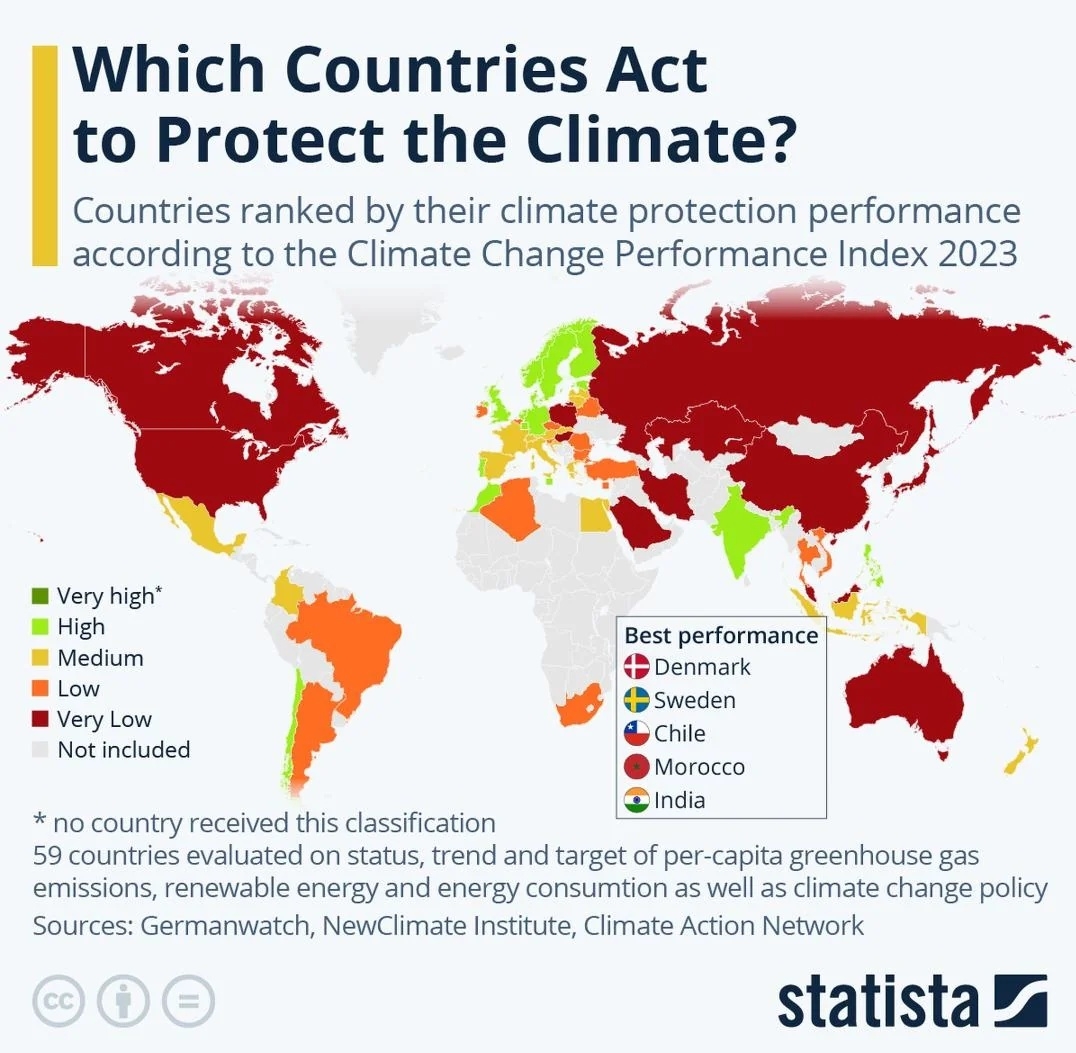









/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)




















