Back
Anonymous 1
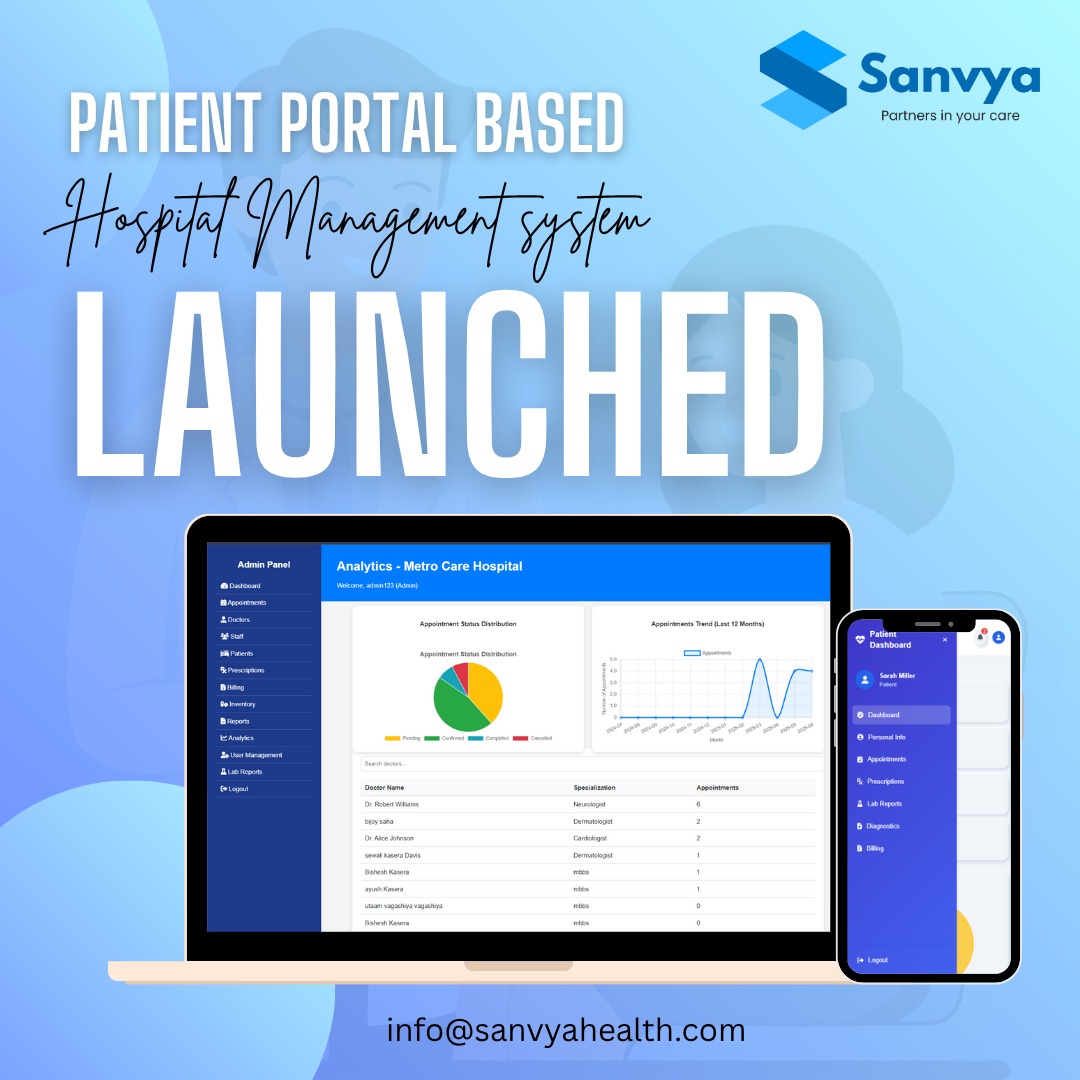
Hey I am on Medial • 1y
This idea sounds amazing in theory, but patient data privacy is a huge concern. Who would manage the data, and how would we protect sensitive info? One breach, and all that private health data could be at risk.
Replies (1)
More like this
Recommendations from Medial
Robin doston
Hey I am on Medial • 6m
Certified Information Privacy Professional/United States (CIPP/US) Exam Overview The Certified Information Privacy Professional/United States (CIPP/US) exam, offered by the International Association of Privacy Professionals (IAPP), validates a profe
See MoreHarshit Vijayvergia
🚀 Legal Professiona... • 8m
🔐 DPDP Compliance Checklist — For Companies (Series) 1 1️⃣ Maintain a Record of Processing Activities (RoPA) → List all personal data collected, processed, stored, and shared. Based on which prepare DPIA under Sec 10 2️⃣ Implement Valid Consent Me
See MoreVasvi Seth
Cyber Security Stude... • 1y
🔒 Protecting Sensitive Personally Identifiable Information (SPII) is paramount in today's digital landscape. SPII encompasses data that requires even stricter handling guidelines to safeguard individuals' privacy and security. As we navigate the co
See MoreSwapnil gupta
Founder startupsunio... • 10m
What would you do if, Users want new features NOW, but regulators demand strict privacy first. 📌You have 2 options- Read Full - https://www.startupsunion.com/blog/business-dilemmas-8/data-privacy-vs-feature-66 #startup #decisionmaking #founder #
See MoreDownload the medial app to read full posts, comements and news.










/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)





















