Back
Replies (1)
More like this
Recommendations from Medial
Kartikey Shukla
Let me help you get ... • 11m
hi there i have been into medial for so long but writing this post about like i want to know is there somebody interested about security and by security i mean security at browsing things security over the internet.. just answer the below poll I'll
See MoreAbdul Alim
Building Lovable for... • 3m
Crazzy Grind Day 24 🔒 Today wasn’t about building or marketing. No tweets. No blog. Nothing. Even Crazzy itself was down. Not because of any bug — I turned it off myself 😅 I noticed something suspicious, so I decided to take it offline and tighte
See More
Zain Abdullah
Cyber Security Analy... • 9m
The Vision "You can't secure what you can't see." When I started building Barqen, I wasn’t trying to create another vulnerability scanner. I wanted visibility, full visibility. What’s running. What’s exposed. What’s misconfigured. What’s risky.
See MorePrakhar Sachan
Fonder @Altravex.ai ... • 12m
🚀 I am curious about what drives your SaaS product development! 🌟 What aspect of building a SaaS product do you find most challenging? 1. Identifying the target market 2. Developing scalable architecture 3. Ensuring data security and compliance 4.
See More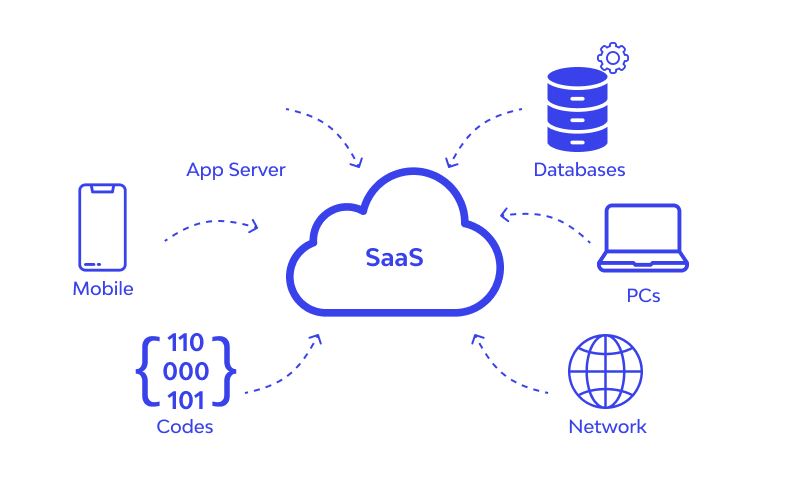
Download the medial app to read full posts, comements and news.











/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)




















