Back
Anonymous 5
Hey I am on Medial • 1y
Make sure you have appropriate monitoring and logging mechanisms in place to track the performance and health of your application. Tools like Prometheus, Grafana, and ELK Stack can help you collect, analyze, and visualize data from your application and infrastructure
More like this
Recommendations from Medial
Vansh Khandelwal
Full Stack Web Devel... • 3m
In today’s data‑driven world 60% of companies struggle with log management. Log management—collecting, storing and analyzing logs—is vital for performance, security, compliance and faster troubleshooting as cloud, microservices and distributed system
See MoreKunal Gavhane
Learn. Write. Share.... • 1y
DevOps Roadmap 🏆 Step 1 – Linux Basics Step 2 – Scripting (Bash, Python) Step 3 – Git Step 4 – CI/CD (Jenkins, GitHub) Step 5 – Containerization (Docker) Step 6 – Orchestration (Kubernetes) Step 7 – Monitoring (Prometheus, Grafana) Step 8 – Cloud P
See MorePratik Raundale
Cloud Devops Enginee... • 6m
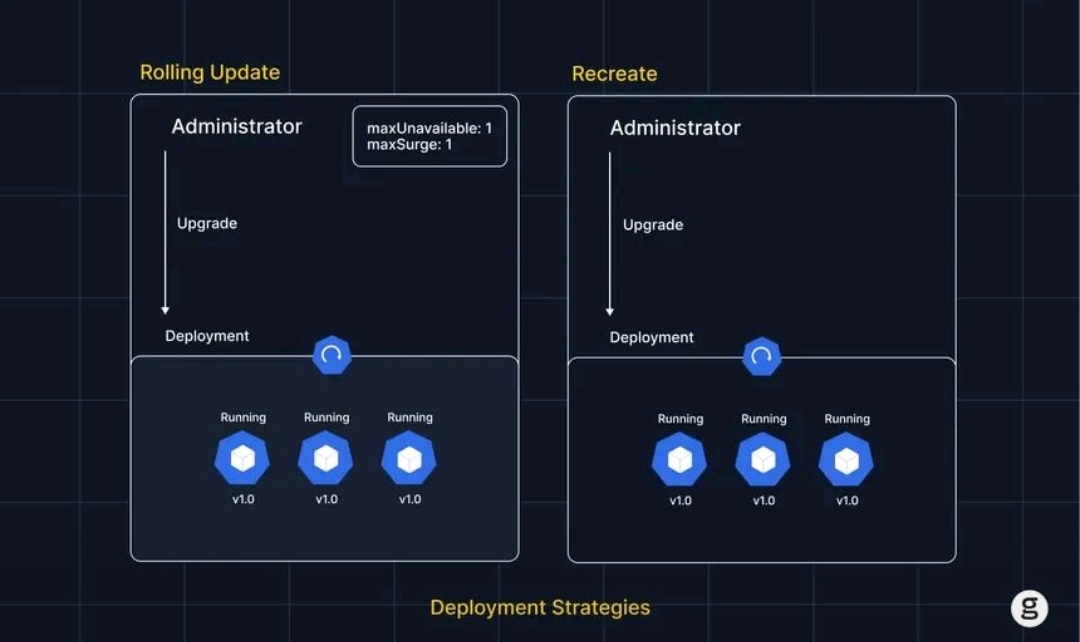
This Week's Learning Journey Kubernetes, AWS & ELK Stack The focus was on container orchestration, deployment strategies, configuration management, and monitoring. #Kubernetes & Deployment Explored Kubernetes architecture including Pods, Services,
See More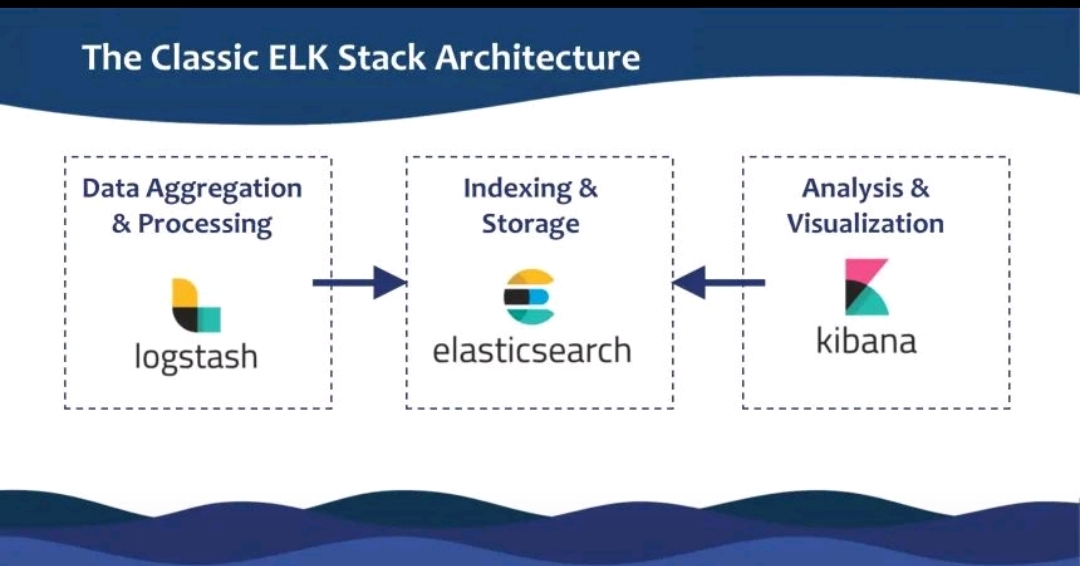
Vasvi Seth
Cyber Security Stude... • 1y
Security logging and monitoring failures can be detrimental to any organization's cybersecurity posture. Insufficient logging and monitoring capabilities pave the way for attackers to exploit vulnerabilities undetected, leaving organizations vulnerab
See MoreHimanshu Singh
Help you to build yo... • 1y
As a backend engineer. You should learn: - System Design (scalability, microservices) -APIs (REST, GraphQL, gRPC) -Database Systems (SQL, NoSQL) -Distributed Systems (consistency, replication) -Caching (Redis, Memcached) -Security (OAuth2, JWT
See MoreRohit Hemnani
AWS devOps Engineer • 12m
Hi Everyone, i am looking for a Job as a DevOps Engineer , i have intern experience and certification with the following skills -AWS(ec2, vpc, cidr, subnet, lambda) -linux/unix -git,github -Jenkins -maven -tomcat -CICD -docker -kubernetes -terraf
See MoreSheikh Ayan
Founder of VistaSec:... • 11m
🔍 Top Log Monitoring Tools for Cybersecurity 🔍 Protecting your digital assets starts with real-time log monitoring! Here are the top log monitoring tools every cybersecurity professional should know: ✅ Splunk – Advanced analytics, real-time monit
See MoreDownload the medial app to read full posts, comements and news.












/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)





















