Back
koushik M
Cybersec • 1y
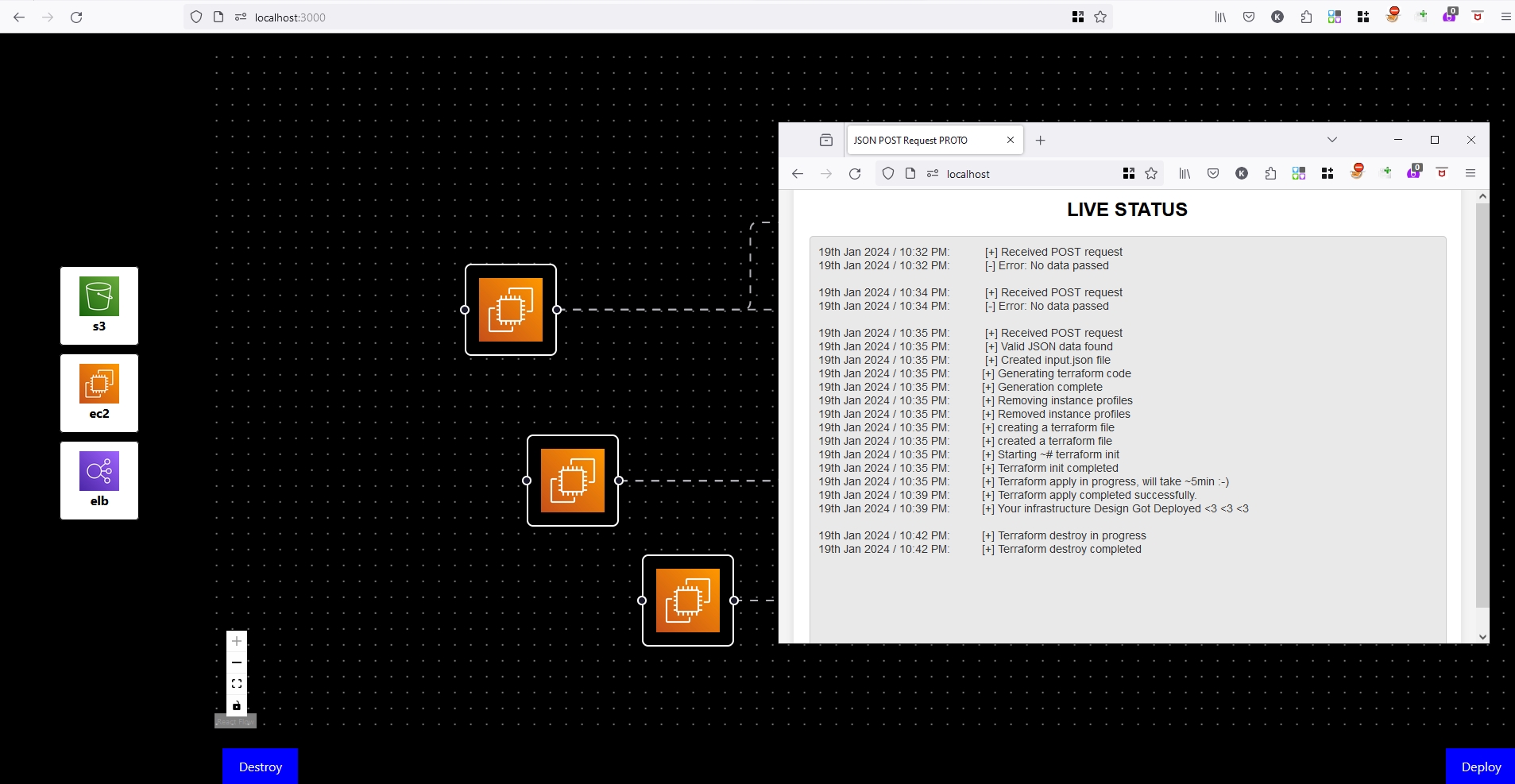
Hi @everyone My product is a virtual playground where you can architect cloud infra effortlessly. It's like having a plug-and-play interface, once your design is ready, a single click deploys it instantly. Additionally, there's a dashboard equipped with Al capabilities. This Al assistant allows you to define policies, security groups, and other technical rules effortlessly. These configurations can be seamlessly integrated into your cloud architecture while designing, ensuring compliance and security while you design. let me know if anyone is interested in this idea so we can work together. Extend the capabilities of the product and get possible investment✨ Below image (prototype) : I have designed basic cloud architecture by dragging the elements to the playground and connecting them. Once clicked on deploy button, all the specified services, security groups, roles ..etc were deployed/created in my AWS account. Design -> IAC -> Deploy insta and LinkedIn are in my medial profile.
Replies (5)
More like this
Recommendations from Medial
Vipul Soman
Cybersecurity Consul... • 10m
How Cloud Security evolved over the years: CSPM → CWPP → CNAPP 1. Cloud Security Posture Management (CSPM) focuses on identifying and remediating cloud infrastructure misconfigurations. It continuously scans your cloud environments against security
See MoreParampreet Singh
Python Developer 💻 ... • 11m
Difference in Google AI Studio vs Vertex AI Studio 👉 Google Al Studio - The fastest way to build with Gemini - Free-web-based developer tool - Google/Gmail account - Prototype and launch apps quickly. with an API key - Data Sharing with Google for
See MoreRajus Kandpal
AWS Certified|| Orac... • 6m
I’m thrilled to share that I have officially passed the AWS Certified Cloud Practitioner exam! ✅ This certification marks an important milestone in my cloud journey, strengthening my foundational understanding of AWS services, cloud architecture, se
See More

Abdul Shaikh
Every Dream is Worth... • 11m
🚫 Al Agents Are Coming-90% Will Fail Without This Key Factor Al agents promise seamless automation and intelligent decision-making, but their effectiveness hinges on one crucial factor: high-quality data. Without clean, structured, and accessible
See MoreVasvi Seth
Cyber Security Stude... • 1y
💻 Embracing Cloud Security: Ensuring Data Protection in the Digital Realm 🔒 Cloud security is more than just a buzzword; it's a critical process ensuring that assets stored in the cloud are properly configured and access is restricted to authorize
See MoreDownload the medial app to read full posts, comements and news.



















/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)



















