Back
Pranav Alonay
Building apps • 2y
I think this whole facad of protecting your data is bs, no offence, but I don't think that big companies having your data is actually harmful for you (unless there is a leak) they just want your data so they can show you personalised ads and i am not completely bothered by it too, so I don't think this idea is viable, I mean the blockchain works at the same principle and we all know what happened to that, for these reasons, I am out😂
Replies (3)
More like this
Recommendations from Medial
Mohd Rihan
Student| Passionate ... • 8m
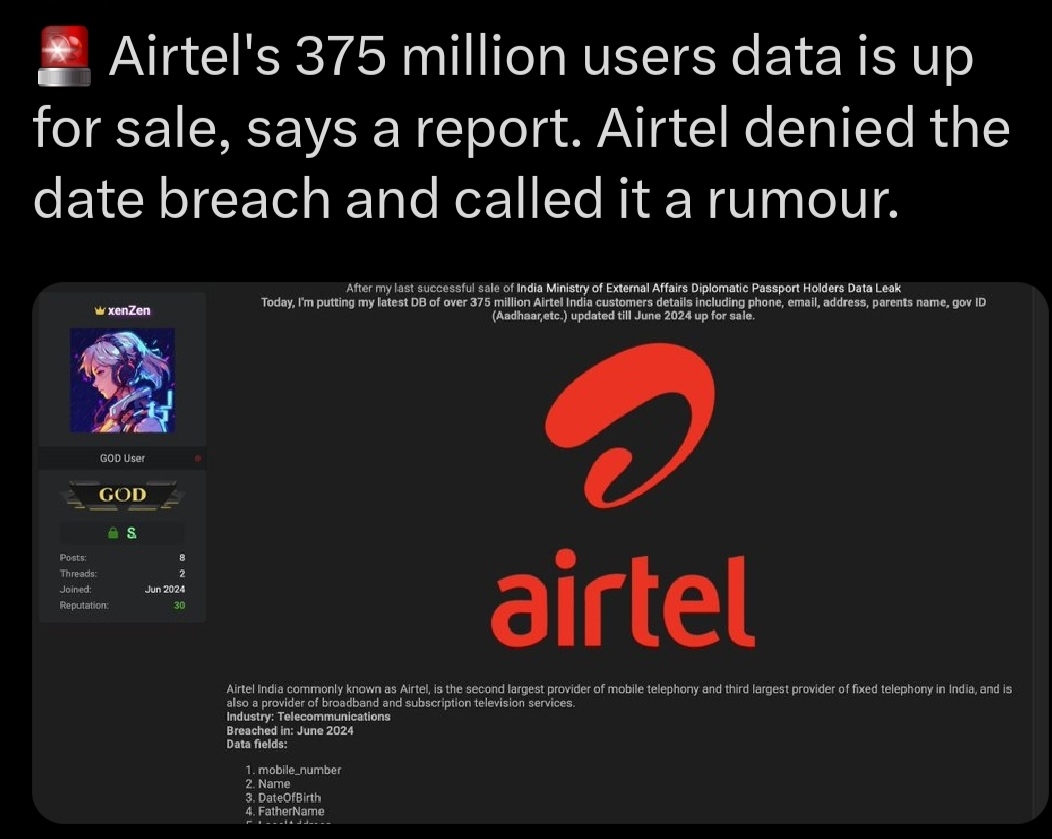
Massive Data Leak Alert: Over 16 billion credentials (usernames & passwords) have been leaked online via logs from infostealer malware like RedLine & Raccoon. These include accounts from Google, Facebook, Apple, and more. Most data is fresh, posing h
See MorePavan SN
Founder of Algoveste... • 1y
Hey Medial-ians, Today I completed an ai software that 1. Automates SEO of wordpress 2. Gets personalised info of the companies data, where you can ask questions and get answers along with graphs. 3. Does research for you and writes articles. do y
See MoreDownload the medial app to read full posts, comements and news.











/entrackr/media/post_attachments/wp-content/uploads/2021/08/Accel-1.jpg)


















