Back
Zain Abdullah
Cyber Security Analy... • 4m
To validate your product, it is essential to assess its market value and determine whether there is a demand for it. After developing a MVP, the next step is to conduct testing. If you have created an advanced enterprise-level file encryption software, how will you identify potential users/clients for testing?

More like this
Recommendations from Medial
Sheikh Ayan
Founder of VistaSec:... • 5m
🔥 Top Exploitation Tools for Penetration Testing 🔥 🔹 Metasploit Framework – The go-to tool for developing, testing, and executing exploits efficiently. 🔹 Cobalt Strike – Advanced red teaming tool for post-exploitation, persistence, and lateral
See Morefinancialnews
Founder And CEO Of F... • 9m
Indian Semiconductor Lab Provides Fab Services to Boost Startup Innovation India's SCL Offers Free Fab Support to Chip Design Startups India's first chip fabrication unit, Semi-Conductor Laboratory (SCL), Mohali, is set to provide comprehensive sup
See MoreTarun Patel
Cybersecurity Analys... • 5m
Hiring Alert: Ethical Hacker Wanted! We are looking for a skilled Ethical Hacker to join our team at Selfsecure. If you're passionate about cybersecurity, penetration testing, and ethical hacking, this is your chance to work with a growing cybersecu
See MoreJewelpik App
House of jewellery b... • 5m
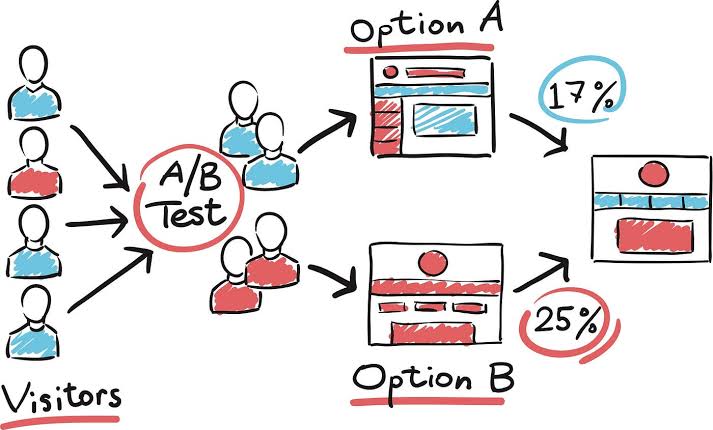
The Importance of A/B Testing in Digital Marketing? A/B testing is a key method in digital marketing that helps businesses make data-driven decisions to optimize their campaigns. It involves comparing two versions of a marketing element (like an ema
See MoreSheikh Ayan
Founder of VistaSec:... • 6m
🔍 Top Forensic Analysis Tools Every Cybersecurity Expert Must Know! 🚀 Forensic analysis is critical in digital investigations, cybercrime detection, and incident response. Here are the top tools every cybersecurity professional should have in thei
See MoreDownload the medial app to read full posts, comements and news.